What Are SD-WAN, VPN, and ZTNA, and How Do They Differ from Each Other?

Remote and hybrid working conditions have become the new standard in the wake of the COVID-19 pandemic, which has unfolded over the past few years. Consequently, remote access systems and networks, which allow for secure access to a company’s infrastructure regardless of time or location, have become crucial.
Especially in the case of larger companies with widespread operation locations, there have been complaints about the challenges in network management. Enabling users to access on-premises systems from outside the enterprise has the potential to enhance work efficiency and convenience. However, it also introduces elevated security vulnerabilities.
Utilizing proper and robust security measures is crucial for safeguarding your assets against security vulnerabilities. Therefore, let’s delve into some of the key technologies commonly discussed to enhance reliability and security when establishing an enterprise network.
SD-WAN

Software-Defined Wide Area Networks (SD-WANs) are gaining prominence due to the increasing use of business applications in distributed enterprise environments, driven by the expansion of cloud environments and technology.
A Wide Area Network (WAN) is a network that links Local Area Networks (LANs) across a vast geographical area. Typically, large organizations utilize WANs to interconnect branch offices in various regions with the central company network.
However, the escalating use of cloud-based applications in contemporary enterprises has imposed significant demands on traditional Wide-Area Networks (WANs), resulting in latency, bottlenecks, and network slowdowns. To solve this problem, the implementation of Software-Defined Networking (SDN) has emerged as a solution, enabling efficient management of network pathways and complex operations while granting users control over the network through software.
SD-WAN is a concept that leverages Software Defined Networking (SDN) principles for Wide Area Networks (WANs). It separates the software-based control functions from hardware-based data transmission, enabling the provisioning of virtualized resources through various connectivity options, such as broadband Internet, dedicated lines, and 5G networks, without the need for specialized hardware.
Although SD-WAN can maximize application performance, its most significant challenge lies in security. Hackers can exploit vulnerabilities to gain access to corporate networks, compromising sensitive data or disrupting network functions. In cases where multiple branches are connected to the cloud, the larger attack surface not only increases the risk of unauthorized access but also escalates potential damage, demanding proactive measures.
VPN

One of the most widely used solutions in remote work environments is the Virtual Private Network (VPN). It provides an encrypted network pathway for secure communication between servers and devices, facilitating secure access to your on-premises network even when working outside the office.
VPNs create secure tunnels for transmitting data over the internet, encrypting traffic to enhance privacy, anonymity, and security, especially when using public Wi-Fi networks, while also helping prevent location tracking.
Many companies rely on VPNs for secure external access to their corporate networks. However, preventing unauthorized access by attackers who have obtained authentication credentials can be difficult, as they authenticate after gaining access to the application.
Moreover, in cases where a user’s device is infected, even if that user accesses the network through VPN, it poses the risk of introducing malware into the internal network, potentially impacting the overall security.
In environments where the boundaries between internal and external are blurred, VPNs are exposed to cybersecurity threats such as hacking and malware infection. These vulnerabilities inevitably impose limitations on today’s cloud-based work environments.
ZTNA

The recent adoption of hybrid work practices regardless of location, such as telecommuting, workstations, and hub offices, has prompted numerous companies to embrace cloud technologies. Consequently, there has been a significant increase in the adoption of Zero Trust Network Access (ZTNA) solutions among organizations.
This is because ZTNA, which operates on the foundational principle of zero trust, ‘Trust nothing, verify everything’ is applied, emerged as a solution to address the limitations of SD-WAN and VPN, as previously described.

To safeguard sensitive data, ZTNA not only validates all users and devices attempting to access the enterprise network but also maintains a continuous requirement for user verification. It remains vigilant at all times, even for users who already possess access, ensuring the security of critical data.Access for remote users is automatically denied unless explicitly granted, and such access is exclusively authorized to trusted entities that have successfully passed identity authentication based on the security policies defined by the enterprise.This approach safeguards on-premises systems against potential threats by rejecting access from unknown users and refraining from placing complete trust in all access attempts. Consequently, the implementation of ZTNA solutions in cloud-based work environments can establish a more flexible and secure network environment, ensuring the protection of data and applications, even when accessed by remote users.As traditional corporate network boundaries blur, it becomes crucial to establish a method of safeguarding and managing all devices connected to broad networks, enabling proactive responses to security threats.
Cloudbric PAS(Private Access Solution)
The Cloudbric PAS (Private Access Solution) is a ZTNA solution with Software Defined Perimeter (SDP) technology.
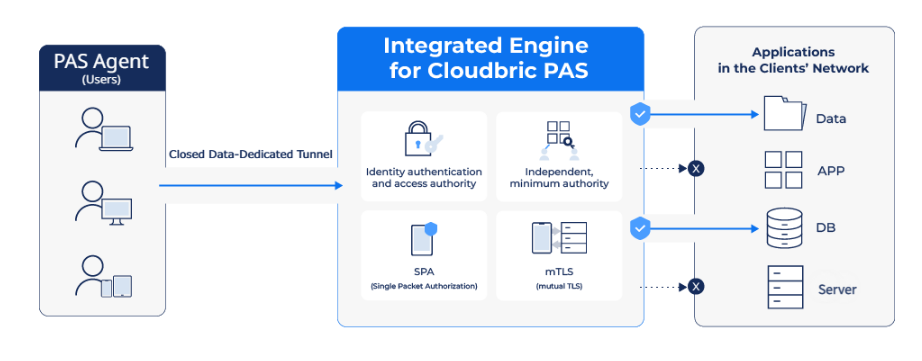
Cloudbric PAS utilizes virtual IP addresses for accessing enterprise networks, thereby safeguarding internal networks by concealing the physical server connection details from external exposure.
Two-factor authentication (2FA) offers user and device identity verification along with optimized security policies per organization and micro segmentation-based access. All these features can be conveniently configured through the user console.

—
As remote work becomes a necessity rather than an option, there is a growing interest in technologies and solutions that facilitate productive work while ensuring the protection of corporate networks. Building a secure enterprise network with solutions like the Cloudbric PAS (Private Access Solution) to meet and optimize specific business requirements.





