Secure Remote Access: A Comparative Analysis of SSL VPNs and SDP

In early 2020, the global onset of the COVID-19 pandemic disrupted conventional business operations, forcing many companies to hastily adopt remote work practices for telecommuting. While some organizations were prepared with pre-existing plans for remote work, the majority faced an unexpected transition.
In response to this rapid shift, companies seeking secure remote work solutions turned their focus to SSL VPNs.
Implementation

Traditionally, numerous companies have relied on private networks to establish a clear separation between their internal and external networks, thereby fortifying the internal networks against unauthorized access from the external sources. While this segregation effectively ensures security within the company premises, it introduces challenges for remote access from locations such as home or other external sites.
With the implementation of work-from-home policies due to COVID-19, many employees faced the urgent need to connect swiftly to their company’s network through their home Internet. This sudden transition posed a significant challenge – the inability to access the company’s internal network, including critical components like mail, payment systems, and groupware, via external devices led to inevitable disruptions in workflow.
In response to this inconvenience, companies proactively implemented countermeasures to ensure secure access to internal systems from external locations. A prevalent solution adopted by many organizations was the SSL VPNs.
What is an SSL VPN?
Before exploring SSL VPN in detail, let’s briefly understand the concept of VPN.
A VPN(Virtual Private Network) is an encrypted network pathway that facilitates secure communication between servers and devices. It allows for protected access to corporate networks from external locations, ensuring a private connection beyond the physical premises of the company.
SSL VPN is a service that integrates VPN with the Secure Socket Layer (SSL) protocol or more recent protocol Transport Layer Security (TLS) to encrypt traffic between web browsers and SSL VPN devices. The familiar lock-shaped icon preceding a website’s URL indicates the current validity and security of the website’s TLS (SSL) certificate.
Combining VPN services with SSL encryption, SSL VPN is a browser-based virtual private network technology that ensures secure communication with private networks.
SSL VPN delivers private IP and routing information following the authentication and encryption process through the TLS protocol. This functionality allows your device to operate as if it is directly connected to an internal network. Since the required TLS protocol is already integrated into all browsers, users of SSL VPN can access the company’s network seamlessly without the requirement for additional software.
Limitations of SSL VPN
While SSL VPN offers the convenience of a browser-based connection without requiring additional software installation, it has limitations that users and organizations should be aware of.
The encryption provided by SSL VPN is limited to the connected browser, leaving other applications on the device unprotected and presenting challenges in diverse service environments. Additionally, potential vulnerabilities in the browser code of SSL VPN require careful consideration, as any weaknesses in the code could compromise the overall security of the connection. Moreover, there is a risk of unauthorized access, particularly in the event of a Distributed Denial of Service (DDoS) attack, which might force a shift in VPN authentication mode to ‘Allow All,’ potentially compromising the security of the connection.
The Rise of Zero Trust and SDP

In response to the escalating complexity of cyber threats and the acknowledged limitations of SSL VPNs, an increasing number of companies are adopting ‘Zero Trust’ principles to bolster security.
Zero Trust is a security concept dedicated to protecting critical data within a company by examining all users and devices connecting to the company’s network, adhering to the principle of “Never Trust, Always Verify.”
Specifically, Software Defined Perimeter (SDP) emerges as a zero-trust solution to replace SSL VPNs. SDP embodies a next-generation, identity-based access control framework that implements Zero Trust Network Access (ZTNA) through an ‘Authentication first then connect’ approach, making it distinct from the traditional model used by existing network security, like SSL VPN with its ‘Connect first, then authenticate’ approach.
SDP technology establishes a connection to the company’s internal network contingent on the results of identity authentication, fortifying defenses against external intrusions and ensuring secure access exclusively for verified users who complete the authentication process.
SDP is structured with agents, controllers, and gateways. It safeguards critical information resources by concealing them with gateways and executes user identity verification and resource access control through controllers. This method thoroughly examines network devices, device status, and user IDs to grant access exclusively to authenticated users and devices. Devices that are not authenticated won’t receive information to connect to the service.
Furthermore, preceding infrastructure authentication and authorization, SDP operates within a Black Cloud environment, where DNS information or IP addresses remain undisclosed. This approach acts as a barrier against potential security breaches, ensuring a secure communication environment.
The SDP-based remote support method offers the advantage of simplicity in deployment and quick utilization of personal devices on the business network. This enables seamless and cost-effective continuity of work.
Comparison of SSL VPN and SDP
Let’s briefly compare the key differences between SSL VPN and SDP.
① Concept
- SDP establishes a network boundary between a specific program on an external terminal and a specific program on an internal server.
- SSL VPN connects an external terminal to a network using a VPN.
② Authentication Method
- SDP employs an ‘Authenticate first, then connect’ approach, providing limited access by separating control and data channels.
- SSL VPN uses a ‘Connect first, then authenticate’ approach, exposing data across a wide range upon authentication completion.
③ Connection (Exposure)
- SDP utilizes an App-to-App connection method, preventing exposure to unauthorized servers.
- SSL VPN exposes all server IPs and open service ports within a virtual private network.
④ Create a Tunnel
- SDP establishes a tunnel between a specific program on an external terminal and an SDP gateway.
- SSL VPN forms a tunnel between an external device and a VPN server.
⑤ Agent Program
- SDP is essential for compliance with Detailed Regulations on Supervision of Electronic Finance.
- SSL VPN is mostly used as an agent in Korea.
⑥ Service Target
- SDP targets users seeking secure access to on-premises servers in a zero-trust environment.
- SSL VPN caters to users connecting to on-premises network resources externally.
⑦ Firewall Operation
- SDP operates with ease using dynamic IP setup by using the White List method.
- SSL VPN poses challenges due to static IP setup by using the Black List method.
⑧ Service Protection
- SDP is highly secure, concealing servers and making it very difficult to hack.
- SSL VPN exposes servers, posing a constant risk of hacking.
Leveraging SDP for Enhanced Security
In traditional on-premise environments, security systems were often implemented in layers at each element and step to establish and operate a network-based security system. In contrast, SDP provides an elevated level of security compared to VPNs, seamlessly integrating with the existing network separation system.
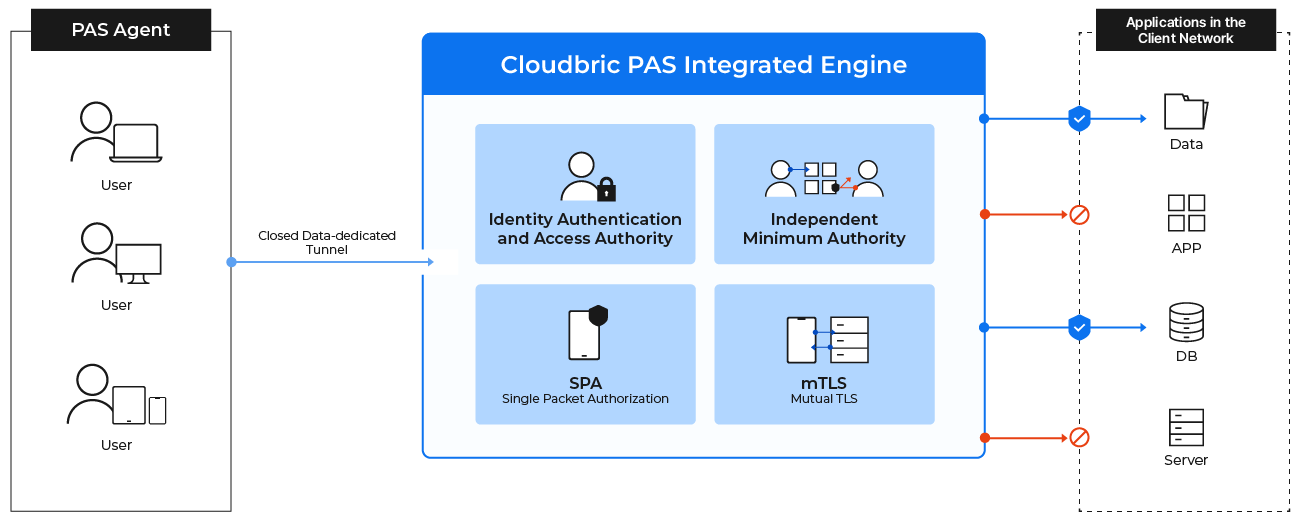
Cloudbric PAS (Private Access Solution) is a SaaS-type zero-trust network access (ZTNA) solution that harnesses SDP technology. By utilizing virtual IP addresses to access a company’s network, Cloudbric PAS ensures the security of the internal network without disclosing actual server connection details to external entities. Moreover, it enhances security through the implementation of two-factor authentication (2FA) for user and device authentication, along with organization-specific security policies and micro-segmentation-based access control for comprehensive protection.
📌 Learn more about Cloudbric PAS >>
Over the past few years, an increasing number of companies, particularly in the U.S., have determined that VPNs are no longer sufficiently secure and are transitioning to SDP methods. Safeguard your enterprise’s network with Cloudbric PAS(Private Access Solution), a SaaS-type zero-trust network access (ZTNA) solution.





