
It’s pretty clear by now that the next frontier for online businesses is to move to the cloud. However, the term ‘cloud’ is still a relatively new idea that can help businesses greatly improve their productivity, efficiency, and save on resource costs. However, this overly anticipated rush to the cloud isn’t without its limitation. One such drawback of the cloud is the possibility for increased web attacks and infrastructure vulnerabilities. Today, we will explore the various ways to help safeguard any confidential information that is stored in the cloud.
Current Cyber Security Landscape
In today’s computing environment, there are an abundance of network and cloud infrastructure providers. But, the question we need to ask ourselves is, “who is managing and tracking all of the inbound/outbound traffic?” In other words, organizations are eager to provide incredibly cost effective and efficient cloud infrastructure, but there hasn’t been much thought or planning surrounding the protection of this cloud infrastructure.
The market is slowly starting to see the effects of improper web protection, however. According to Gartner, by 2020, more than 60% of web applications will be protected by cloud service Web Application Firewalls. Just as fast as people are looking to upgrade to the cloud, there is a growing interest on how to protect these next generation infrastructure solutions. In essence, companies and online website owners are starting to become more proactive, but the job doesn’t end there.
How Do We Protect Ourselves?
The very nature of the internet is to be open, but this could ultimately leave one to be vulnerable to web attacks if not careful. This is the ultimate cloud fallacy. As much as we want to move towards sharing resources, infrastructure, or testing new innovative solutions, this can only be done to a certain degree. Until recently, most companies have been looking to fortify their internal networks and systems to prevent any attacks. The issue is that the internet was designed to freely share and communicate information with the open world. The best way to work around this predicament is not to block ourselves in by building higher walls, but to build smarter gateways. Two ways that we can achieve this is to utilize a perimeter based Web Application Firewall and Database Encryption technology.
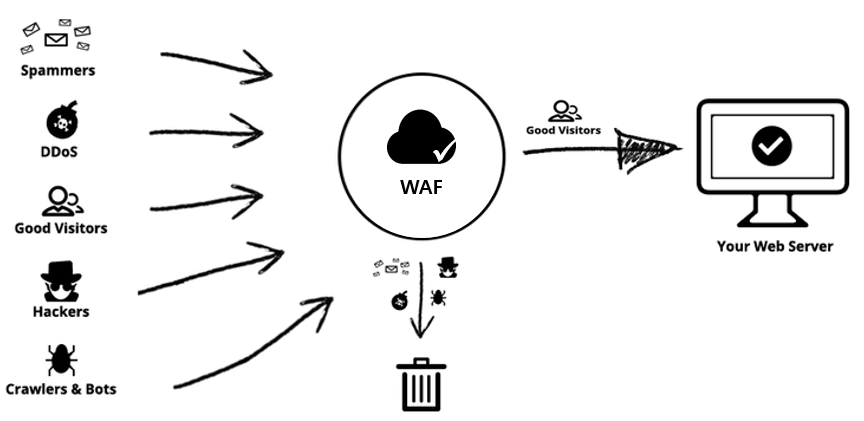
Web Application Firewalls (WAF)
WAFs can help protect all inbound and outbound traffic that flows through the web/application layer (OSI Layer 7). These days, as more and more websites rely on dynamic web applications to power their sites, the vulnerabilities of these applications continue to persist. WAFs are perimeter based web security solutions, which means that they look to monitor all HTTP/HTTPS traffic to sift for any malicious or suspicious web behavior. Once detected, WAFs can automatically block any web hacking attempts that target a web application and ultimately intend to steal sensitive data on a web server/backend database. WAFs can be your first line defense to protect your online business from web attacks when you least expect it.
There are various benefits to implementing a WAF solution into your cloud web security profile, such as:
- Cleaner & safer network – mitigate major hacking incidents
- Peace of mind – always active security that works on the perimeter
- Performance – security that doesn’t affect performance or incur latency issues
- Compliance – satisfy PCI-DSS requirement 6.6

Database Encryption
Database encryption software transforms data stored in a backend database into “cipher text”, which can make the data incomprehensible without first being decrypted. In the event that a web hacker was able to bypass your first line of defense (in very rare instances or caused by rogue insiders), a high performance database encryption software could be your savior. DB encryption software not only prevents sensitive data leakage, but even if data is stolen, encrypted data will be deemed useless since web hackers will be unable to decrypt the information. As an added measure of security, database encryption companies, such as MyDiamo, can separately store database keys into third party key management servers to eliminate any possibility of a data breach.
Here is a short list of the benefits of using a database encryption software:
- Protect Data Completely – encrypted data information is protected, even if it is stolen
- Guarantee Data Integrity – easily detect whether data was manipulated/tampered
- Compliance – satisfy legal & internal/external audit guidelines (HIPAA, SOX, PCI-DSS, etc.)
The key to protecting data stored in the cloud is to take a more perimeter based proactive approach. It’s best to secure your more sensitive data before cyber criminals ever reach your vulnerable web applications. This can be accomplished by utilizing a Web Application Firewall and Database Encryption software as an added security insurance. Get started on protecting your data in the cloud today!
For more information, check out this great presentation about protecting sensitive data stored in the cloud given by our SVP of Business Development, Jaeson Yoo, at the Cloud Security Expo in London!





