DDoS are nothing new; the first DDoS attacks started back in 1996. But many gave them no attention until 20 years later, in 2016, when the feared DDoS Mirai botnet infected thousands of IP-based web-cams with “cheap bandwidth” which brought down major websites.
Now, the techniques are evolving.
In this post, we’ll review the evolution of DDoS attacks. How they started, and what they have become—the new techniques being used by hackers. Then we’ll give you a quick checklist on how to protect yourself and your most important business assets.
 So, what is a DDoS attack? How do they work?
So, what is a DDoS attack? How do they work?
A DoS (Denial of Service) or DDoS (Distributed Denial of Service) are types of cyberattacks that aim to disrupt a service— from slowing down a website to shutting down an entire network. When something is compromised with a DoS attack, legitimate users, employees, or subscribers cannot use the service— until it is restored. Hackers conduct a DoS attack by sending too many requests to a target that is legitimately listening and attempting to reply. But the target does not have the capacity to handle massive requests, so it starts to fail. But if the hacker does not have the necessary resources (processor and bandwidth), the requests will not be so powerful and frequent. So DoS attacks are barely successful anymore, as there are more powerful receiving targets.But when hackers hire an army of zombies? Things change!
Difference between DoS and DDoS?
A DoS attack is carried out by a single source (one machine), while DDoS is carried out by many sources (known as bots or zombies), and their coordinated swarm is also referred to as the Army of Bots.A DDoS is deadly because it does the same as a DoS but instead uses a collection of machines working simultaneously to take down a single target. Think of DDoS attacks as a rush of thousands of hungry visitors going into a restaurant demanding the entire menu. Without the resources to reply or stop hungry visitors, the restaurant will not serve other customers. The service will inevitably break down!
How does a hacker perform a DDoS?
Let’s look at the picture below. 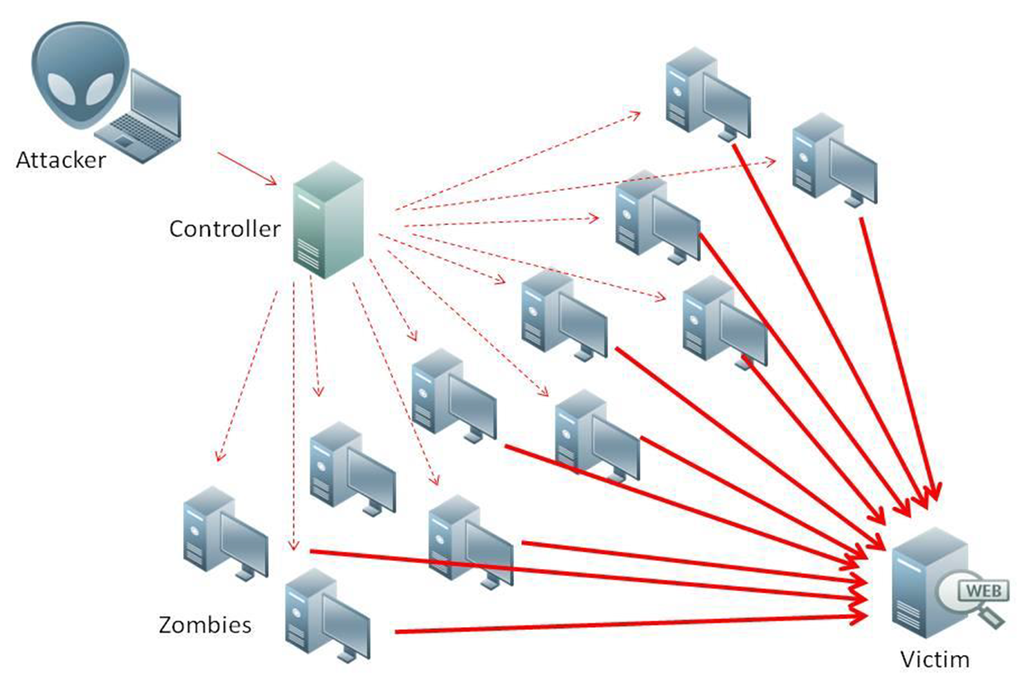
- The attacker hires the army. The first thing the DDoS attacker needs is to infect as many machines as possible with a backdoor controller, usually via a virus.
- Coordinates the army. When the attacker gains control of every zombie (infected machine), it is capable of orchestrating them via a controller (or proxy).
- Attacks a single victim. All that it takes by the attacker is to use a script or tool) to select a target and craft the attack with large TCP/UDP messages (layer 4) or HTTP requests (layer 7) sent by all zombies and configure large packet timeouts.
What motivates a hacker to do a DDoS?
Most DDoS attackers are inspired by the pure black-hacking evil, others by hacktivism, and a few others by monetary gains. It has been proven that either old and new DDoS attackers, most of the time, have been driven by the desire to portray power.
How did DDoS attacks get to be so effective?
The first registered DDoS attack occurred in 1996, when Panix, an old ISP was hammered by an SYN flood (layer 4)— the oldest DDoS trick in the book. After that attack, hackers took interest and began exploiting other system’s vulnerabilities. The “Ping of Death (PoD)” a simple yet powerful attack, takes the advantage of the ping command (layer 3) and its ability to modify ICMP packets larger than 65,535 bytes. PoD does not arise from the vulnerability of the source, but an inability by the destination to filter malformed large pings. Sending oversized packets can make any system’s memory overflow to easily crash. Another popular type of DoS attack is the HTTP Flood, which doesn’t need malformed packets as the PoD, but performs the attack at the application (7) layer. The HTTP Flood uses legitimate-looking HTTP GET or POST requests to target and compromise a web server or website.
Why are new DDoS so effective, regardless of the OSI model layer?
So even using the most oldest trick on the DDoS book, the TCP SYN, with an army of bots can make high-profile websites, such as GitHub, Twitter, Reddit, Netflix, and Airbnb inaccessible. This is exactly what happened in 2016, when Dyn, a DNS service provider was taken down by a large army of IoT-infected devices with the infamous Mirai Malware. That same year (2016), the DDoS Mirai Botnet attack targeted the cybersecurity blog Krebsonsecurity, which suffered an excess of 620Gbps traffic from about 600,000 compromised IoT devices including IP-cameras, NVRs, home routers, etc. In 2016, Mirai had momentum. The same Malware infected 152,000 IoT devices (mostly vulnerable webcams) broke down the European web hosting company OVH. This DDoS attack accomplished a world breaking record of 1.1 Tbps disruptive traffic coming to the web hosting company. This Mirai Malware episode marked a new era of DDoS attacks.
Why do we need to be aware of DDoS in 2020, and moving forward?
Today, unfortunately, there is a lot of underground movement on the dark web. Hackers create new DoS variations from open source-code and share it with their fellow hackers on dark web forums. The Mirai Botnet source code, for example, was easily accessible as open-source code in a hacker forum. So, Mirai continued to evolve and create havoc around the world. Below is a list of new DDoS variations found beyond the Mirai attack that you should continue to be wary of as we close off 2020.
1. The Fight to Infect More IoT.
The difference between today’s DDoS attacks versus a couple of years back is the expanded technology’s footprint. With IoT, the attack surface is more extensive; there is a pervasive, ubiquitous communication that can be reached easily. IoT attacks can leverage from one vector and faster (more packets per second).Before Mirai 2016, nobody believed that a DDoS attack could be so powerful. But the sophistication and destruction of the Mirai Botnet attack gave way to another level of DDoS. IoT Botnet campaigns such as Mirai and Gafgyt evolved. Mozi Botnet, for example, now targets more IoTs than Mirai and Gafgyt combined. Mozi botnet targets misconfigured IoT devices through the use of Command-injection (CMDi) attacks.
2. The Memcached DDoS
In mid-2018, Akamai and Qrator reported a larger and more powerful DDoS threat than the Mirai botnet— the Memcached Vulnerability. Memcached is a standard Linux service that comes by default. The service is found on cloud servers that are exposed to the Internet. It uses UDP and communicates without authentication. Attackers don’t even need to “infect” a vulnerable server; they only create a fake address and send requests to a target.According to Akamai, the Memcached DDoS attack is the largest ever detected and twice the Mirai Botnet size.
3. Combining Ransomware-model
DDoS attacks are also following a new approach. Attackers are no longer concerned with showing power or taking down a site for political reasons; now, they are starting businesses based on the ransom-model. They’ll threaten companies with a DDoS attack by sending extortion letters demanding “ransom” money. If a company doesn’t pay the ransom, they’ll limit the services. To prove that attackers have control of the company, they’ll execute a smaller-scale DDoS attack on the day they send the extortion letter.
4. DDoS-for-hire and Botnet as-a-Service
Sadly, the dark web is filled with lots of “hire-a-killer” kinds of services. Now, malware also takes a chance in the Botnet-As-a-Service model. The Trickbot banking trojan, for example, is a persistent modular Trojan used to steal banking credentials, spread ransomware, and used in botnet attacks. But if you don’t want to get your hands dirty, you can still hire a “killer.” There are online DDoS-for-hire attack services, such as vDOS Stresser, that helps coordinate large scale DDoS attacks (more than 150,000). According to Krebsonsecurity, the vDOS company earned close to $600,000 in two years by coordinating the attacks.
5. CLDAP Reflection DDoS Attacks
The first Connectionless Lightweight Directory Access Protocol (CLDAP) Reflection DDoS vulnerabilities were found around 2016. The attack uses vulnerable third-party CLDAP servers as bots and is paired with an amplification attack method to make things 50x to 70x times worse. Right at the beginning of the COVID-19 pandemic, a massive CLDAP Reflection DDoS attack in February 2020 surprised the world’s most predominant public cloud provider, AWS. The attack targeted an AWS customer with a registered attack that lasted for three days. It had a peak of 2.3 terabytes/second of junk traffic— something never seen before. Although it didn’t cause much service interruption, it could have been tremendous havoc.
So how to defend from new DDoS attacks?
So previously, we learned about DoS and DDoS attacks. We also went through the most historical cases of DDoS attacks and their evolution. How can we protect from these attacks? How can we mitigate DDoS attacks? What are the most popular techniques to defend from DDoS? The following are three questions you can ask to avoid being a part of a botnet or being the target.
- How not to become a bot in a botnet?
- How to prepare for an attack?
- What to do during an attack?
How not to become a bot in a botnet?
Educate the users of the network/system on specific cybersecurity rules. First and most, avoid social engineering techniques, including spam, phishing attempts, and avoid pirated software, including trojan horses. Secondly, ensure AAA (Authentication, Authorization, Accounting) policies are in place, such as MFA, strong passwords, fine-grain levels of authorization, etc. Ensure users (or you) are using a firewall and are protected against zero-day attacks with the latest antivirus software. A firewall will ensure no open ports give malware entrance and antivirus that there is no malware present in the system. Remember, a trojan or malware may contain the script to make your computer another bot in an army of bots. Additionally, never use or buy just any IoT device. Some IoT manufacturers never do diligence security testing and don’t have security compliance. IoT devices are the first and easiest recruits for an army of bots.
How to prepare for an attack?
- Patch systems with the latest updates. Update computers, mobile phones, thermostats, DVRs, home routers, firewalls— anything that is connected to the Internet.
- Distribute workloads and data. Using a CDN (Content Delivery Network) to distribute data helps mitigate the strength of some attacks. CDN will not stop a DDoS attack, but they will help avoid the single point of congestion.
- Configure firewalls to filter out potential DDoS traffic. For example, Ping of Death attacks can be stopped at a firewall. Never completely block an ICMP ping because it is useful, but selectively block fragmented ping messages.
- Use a Smart Web Application to protect Internet-facing assets. During an attack, the best type of defense is a “filter,” in the form of either network or application firewalls. Cloud-based filters take all your traffic, analyze it, and separates malicious traffic. The best DDoS mitigation filters can keep track of connections, are aware of blacklisted IPs, may perform DPI (Deep Packet Inspection) at layer 7, and can limit the rate in case of suspicious DDoS.
What to do during an attack?
Set up a filter!Cloud-Based Web Application Firewall (WAF+) is an advanced cloud-based web application protection tool. WAF+ is similar to a Web-Application Firewall (WAF) but backed up with Artificial Intelligence (AI) deep learning. It can detect web attack patterns (such as basic DDoS crafted packets) and filter out malicious traffic. The WAF+ solution is combined with DDoS protection and an SSL-as-a-Service, to provide a fully comprehensive web site protection. Cloudbric’s WAF will actively block layers 3, 4, and 7 DDoS attacks. When using WAF with a CDN, the protection can be scaled up to 20Tbps of junk traffic. To take it to the next level, the fully managed web security service from Cloudbric, provides comprehensive web security with a variety of services, including:
- Versatile deployment
- Proactive threat protection
- Free SSL & DDoS Protection





