The entire DDoS attack landscape is changing. Although originally intended to inflict damage by utilizing massive traffic, DDoS attacks have become more pervasive, persistent, obscure, and sophisticated. Additionally, the DDoS attack surfaces continue to grow, as IoTs develop and people become increasingly dependent on the internet. This larger “playground,” makes it more convenient and enticing for DDoS attackers to target anyone they choose, which results in a shift in their motives as well.
 1. The Changing Landscape of DDoS
1. The Changing Landscape of DDoS
IoT devices experienced unprecedented growth in 2016 and 2017. During this period, countless devices without proper security standards and measurements were manufactured and sold. Many of these unpatched IoT devices were (and still are) infected by malware such as Mirai or BrickerBot, which make them part of botnets for DDoS attacks. Those same years also saw the rise of usage for Botnets-For-Hire. In fact, in 2017 the FBI, issued a warning about booter and stresser services. The report revealed that these services allowed inexperienced but highly motivated cyber actors to perform DDoS attacks.
In 2018, although no longer a novel idea at that time, attackers started to use more single-vector reflection and amplification DDoS attacks. This year marked a new beginning, heralded by a Memcached vulnerability with an amplification factor of 10,000 – 51,000— something which was never seen before.
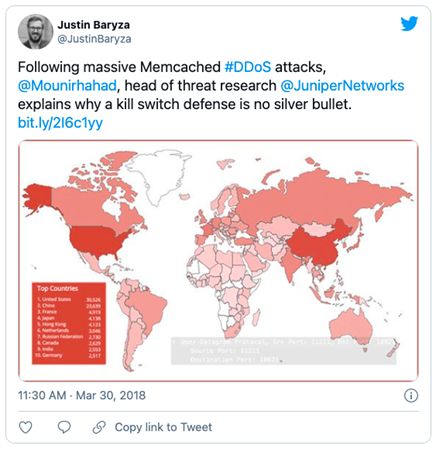 Amplification and reflection DDoS attacks use floods of malformed UDP or TCP packets to bring down targets with massive volumes of traffic. These attacks require creating a malformed packet with spoofed information and using bots with vulnerabilities or infections to reflect (and amplify) traffic to a victim. For now, these types of DDoS attacks are being detected and mitigated faster. For example, GitHub mitigated a massive volumetric (Memcached) DDos attack in 2018 in only 20 minutes. However, these types of attacks are highly likely to grow and expand due to the advancements of IoT.
Amplification and reflection DDoS attacks use floods of malformed UDP or TCP packets to bring down targets with massive volumes of traffic. These attacks require creating a malformed packet with spoofed information and using bots with vulnerabilities or infections to reflect (and amplify) traffic to a victim. For now, these types of DDoS attacks are being detected and mitigated faster. For example, GitHub mitigated a massive volumetric (Memcached) DDos attack in 2018 in only 20 minutes. However, these types of attacks are highly likely to grow and expand due to the advancements of IoT.
COVID-19 Transformed the Attack Surface.
When the COVID-19 pandemic hit at the beginning of 2020, there had been a significant surge of DDoS attacks. As everyone moved to the online realm for their day-to-day activities, including education, healthcare, shopping, and remote work, the entire focus shifted towards the Internet. The overall pandemic conditions (including fear) created a new surface, and the DDoS attacks soared.
The FBI issued a report in 2020, stating that cyber actors were starting to disrupt K-12 educational institutions and third-party services supporting remote learning, via DDoS attacks.
Still, today, many people have no (and still don’t have) idea about how to stay safe online and do not know how to respond in critical scenarios.
2. The Top Four Practices and Types of DDoS Attacks Used Today
The growth of IoT and connected devices with vulnerabilities continues to create a huge attack surface. Plus the availability of Stresser tools and botnets-for-hire services allows anyone, including even those with amateurish skills, to initiate an attack.
The following are some types of DDoS attacks more prevalent today.
A. The Stateful Exhaustion DDoS Attacks
These attacks target stateful servers, such as load balancers or firewalls that maintain the current TCP state and session information. This type of attack intends to fill their TCP state tables with fake connections.
Stateful Exhaustion DDoS attacks can take down underlying network infrastructures such as DNS or SSL/TLS endpoints which are responsible for providing services to end-users. An example is an SSL/Encrypted attack or invalid DNS query attacks.
A real-life case of a stateful DDoS attack is the infamous DYN attack in 2016, which targeted DNS infrastructure and its services to disrupt the service of high-profile websites including PayPal, Visa, Netflix, or GitHub.
B. Application Layer L7 DDoS Attacks
Layer 7 (L7) DDoS attacks aim to exhaust the resources of application layer protocols such as HTTP, SMTP, FTP, SIP, RDP, SSH, and NTP by exploiting their vulnerabilities. Examples of these attacks are HTTP floods (GET and POST headers), SSL negotiation attacks, and the Slow-and-Low (or Slowloris) attack.
Typically, these types of attacks generate small to medium levels of traffic because L7 protocols generally implement stronger message control and security systems. To succeed, these attacks need to be leveraged from large botnets. L7 application attacks are difficult to spot because they look like legitimate traffic. In fact, L7 DDoS attacks could be easily mistaken as normal traffic spikes legitimately triggered by national events or holidays.
C. Multi-vector DDoS attacks
DDoS attackers are beginning to target multiple points of entry (attack vectors) at the same time, to increase the variability, volume, and success rate of an attack. The most common attack vectors usually come from UDP floods, including CLDAP, NTP, DNS, and SSDP but they could also come from TCP and Layer 7.
Multiple attack vectors are sometimes targeted simultaneously to consume more bandwidth and packet rate. Multi-vectors can also be executed one at a time to make attacks less damaging, but longer and more persistent.
Nowadays, multi-vector attacks such as the Burst Attacks and Advanced Persistent Denial-of-Service (APDoS) can create more havoc than a single volumetric attack.
D. DDoS Attacks Begin to Use Automation
Attackers are starting to use AI-based DDoS attacks. They use advanced automated and dynamic techniques to scan the web, find vulnerable bots and make the attacks more persistent.
The AI-based DDoS attack will run AI models from the command center to adapt their attack strategy based on the victim’s mitigation response. They will mount an attack, analyze the response, and dynamically adjust their parameters and vectors to counter whatever defense strategy they confront.
3. Motivation is Transforming
Although Hacktivism-motivated DDoS attacks are slowly decreasing, there still seems to be some movement. For example, the infamous hacktivist groups Anonymous targeted Mexico’s Supreme Court in 2020 to protest police brutality (source). Political and social motivations are now turning to cyberwarfare. For example, the FBI reports Iranian state-sponsored ATP actors threaten election-related systems.
However, the majority of DDoS in 2020 and 2021 appears to be motivated by financial gain. The DDoS Extortion Campaigns are exploding in popularity lately. Cyber actors are sending extortion letters threatening victims of their plan to start, continue, or ramp up a DDoS attack unless they receive a hefty ransom.
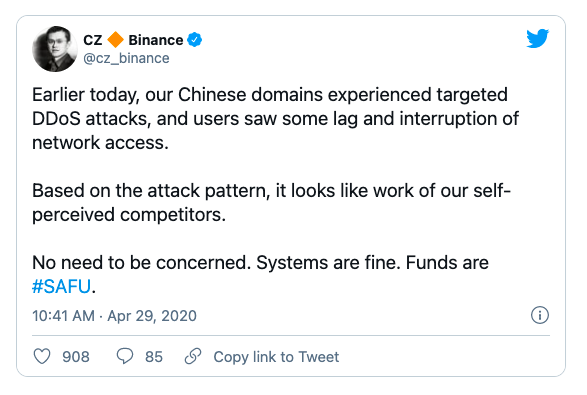
Outside hacktivism, cyber warfare, and financial gains, DDoS attackers also seem to be motivated by competition and market gain. For example, Binance suffered a DDoS attack in 2020. They concluded that the attack was generated from the competition.
 Another unusual but real motivation is when cyber attackers want to attain fame or prove their skills to the world. A Twitter user announced every step of DDoS attacks against WoW (Blizzard game) and Wikipedia over the social media platform. The account was later suspended.
Another unusual but real motivation is when cyber attackers want to attain fame or prove their skills to the world. A Twitter user announced every step of DDoS attacks against WoW (Blizzard game) and Wikipedia over the social media platform. The account was later suspended.
DDoS attackers are also trying to find other targets to inflict more damage. For example, the FBI issued a report on February 17, 2021, about the negative impact that new Telephony Denial-of-service (TDoS) attacks could have on call centers, which affects their availability and readiness. A TDos can overwhelm telephone systems, making them unavailable and unprepared. This can have devastating consequences for first responders and emergency services.
4. Basic Measures to Mitigate a DDoS Attack in 2021
Stopping all DDoS traffic is unfeasible. However, its impact can be greatly reduced to ensure that services can return to normal as soon as possible.
The best solution against a DDoS attack is to plan and start today!
Basic Measures
A. Patch and Update
To avoid being a part of botnets, patch and update anything that is connected to the Internet.
A few days after the Memcached DDoS attacks from GitHub and NetScout, people feared that DDoS attacks would not only continue to happen but also grow in size. However, the opposite happened. There was an immediate decline after as Linux pushed for patching and update efforts.
B. Distribute Data and Workloads
Use networks of proxies (Content Delivery Networks – CDNs) to distribute data and workloads closer to the network edge. In other words, decentralize the origin of the traffic. A CDN will not stop a volumetric DDoS attack but will help absorb it.
C. Use DDoS and Bot Attack Protection Solutions
Use an intelligent filter to protect Internet-facing assets. A cloud-based or on-premises filter can receive all incoming traffic, analyze it, and separate legitimate from malicious traffic. A DDoS protection solution should provide intelligent filtering mechanisms, perform DPI for Layer 7 traffic inspection, and be aware of threat intelligence (blacklisted IPs).
Cloudbric’sWAF+ is an advanced cloud-based web application protection solution. This security-as-a-service is backed up with Artificial Intelligence (AI) to detect web attack patterns, such as DDoS crafted packets, and can filter out malicious traffic.
Cloudbric’s WAF+ can actively block DDoS attacks for layers 3, 4, and 7. When using SWAP with a CDN, the protection can be scaled up to 20Tbps of traffic.





