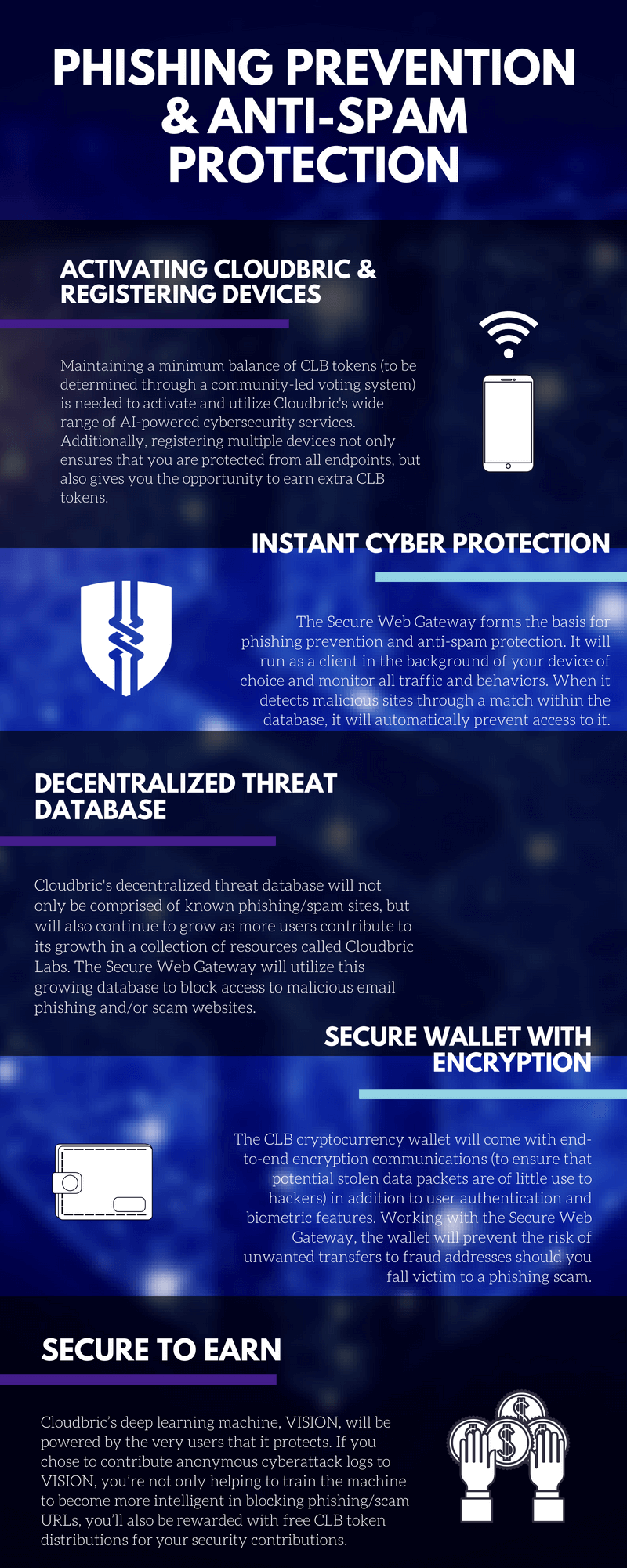
As a decentralized universal security platform that provides a diverse suite of security services, there are many personal use cases for Cloudbric. One can be focused on the prevention of phishing scams.
Phishing is arguably one of the most popular methods among hackers in extracting sensitive information. Shockingly, phishing attempts have grown 65% just in the last year, and according to Webroot, 1.5 million new phishing sites emerge each month.
Phishing Protection Through the Secure Web Gateway
Cloudbric will assist in protecting users against phishing through the Secure Web Gateway by providing instant protection against not only phishing sites but also malicious files and URLs, fraud crypto addresses, and other spam sites. As such, phishing protection will be leveraged by decentralized data collected by Cloudbric Labs as users report these phishing sites to build onto the database.Phishing scams know no boundaries. They target all kinds of users, from SMBs and businesses to government agencies. More importantly, you can find them in almost every industry. The hype surrounding cryptocurrencies (alongside the rise in ICOs), for example, has led to an exponential increase of phishing attacks by hackers.While the blockchain technology may be secure, cryptocurrency is vulnerable to hacking nevertheless. Cryptocurrency assets are just like other digital/virtual assets (email, websites, online accounts, etc.) and therefore can be compromised through some of the most common hacking techniques like phishing. That’s why one of Cloudbric’s strong use case examples can be linked to phishing protection/prevention.
Protecting Your Cryptocurrency Against Phishing Scams
Phishing is one of the most predominant ways in which hackers end up getting access to your private key and ultimately, crypto funds. A typical phishing scenario involving cryptocurrency may play out like this: A hacker sends out a convincing email or text claiming he or she is legitimate entity (like your wallet) but actually link users with malicious links. Through a copycat site, users may end up believing the site is legitimate and in the process enter their private information. The hacker then is able to extract funds from the victim’s address to put in his or her own wallet. With cryptocurrency, once the funds are transferred to a malicious party it’s almost impossible to get them back.Phishing sites, including those cryptocurrency copycat sites that attempt to steal your crypto wallet credentials, are the type of sites that will be included in Cloudbric’s decentralized cyber intelligence database. In the next section, we’ll present a use case example that can better explain just exactly how Cloudbrics works in the prevention of phishing scams.
Cloudbric Use Case Example: Phishing Prevention
Mary falls victims to a phishing scam and is looking for a way to prevent it from happening again.Mary recently got hacked while online shopping. After some unauthorized purchases were made to her account, Mary become determined to not have something like this to happen again. After doing her research on various cybersecurity solutions, she decides to enlist the help of Cloudbric’s services.To register devices and utilize cybersecurity services she will need to download the Secure Web Gateway. Mary decides she wants to register both her smartphone and tablet. However, before that — as part of Clourbric’s token staking and governance policy — Mary will need to make sure she has X amount of CLB tokens in her Cloudbric account in order to starting using the services. (The minimum CLB activation balance will be determined by the community through a voting system on a quarterly basis — though Cloudbric will set the initial minimum balance rates for account activation and security rewards program distributions.)Mary recently got into cryptocurrency, so she also decides she wants to use the Cloudbric CLB wallet after learning that it provides secure token storage — thanks to its encryption and authentication features. After securing and depositing the appropriate amount of CLB into her account, Mary has gained full access to the Secure Web Gateway and wallet.One day, Mary receives an email from her HR department that her company’s regional manager is birthday is coming up and because he’s such a crypto enthusiast suggests gifting him with crypto and also provides his wallet address in the email body. Unbeknown to her, the email seemingly coming from her HR department is actually a scam. Mary copy and pastes the address link to transfer crypto to her “colleague” but the transfer is blocked.Without even knowing it, Cloudbric’s Secure Web Gateway was running in the background the entire time, monitoring any suspicious behavior, and when Mary attempted to transfer crypto out of her wallet, Cloudbric detected a fraud match within its database and immediately blocked and prevented the transfer on behalf of Mary. Thanks to our decentralized database comprised of fraud crypto addresses, wallet owners can be rest assured that they are not moving their crypto to the wrong party.
Cloudbric’s second use case will focus on anti-spam protection and for a good reason too. Spam sites account for 45% of all emails sent. That’s almost half of your incoming mail! Additionally, it’s estimated that approximately 14.5 billion spam emails as sent everyday. Nowadays spam isn’t solely restricted to email. Social media and other online platforms have opened up new venues for spammers to capitalize on and expand their reach.
Cloudbric’s Secure Web Gateway aims to leverage user-sourced threat intelligence to block spam sites in real time.
Cryptocurrency Exchange Sites
It’s no secret why cryptocurrency exchange sites are being targeted by scammers. Just how important are exchange websites in the crypto world? Cryptocurrency exchanges sites supply the platform to trade with other cryptocurrencies, which means your cryptocurrency could be stolen if you end up falling victim to a scam website where you input your credentials.
A spam cryptocurrency exchange website may look legimtiate but upon further inspection there are subtle differences between the original and the copycat site. The site may contain a one letter difference in the URL (try distinguishing between rn and m for example) or use the unencrypted version of the site (HTTP vs HTTPS). These scam websites may lead to cryptocurrency theft or losing access to your account if you aren’t careful.
In the following section we explain a use case scenario that better explains how Cloudbric will block spam URLs. It’s not just spam site URLs, however, it could be malware infected files/PDFs URLs, spyware sites that can also be automatically blocked so long as the Secure Web Gateway is enabled.
Cloudbric Use Case Example: Anti-Spam Protection
Sam is nervous about exchanging crypto due to a rise in spam sites.
Sam finds out about a new cryptocurrency on the market that he’s eager to trade with. He has accounts on different exchange sites since he is looking for sites that support various coins and are available in multiple languages.
Unfortunately, Sam was so eager to trade his crypto on one of the exchanges sites he is uses (www.bitmex.com) that he mistakenly wrote the URL wrong with only one letter difference (www.bittmex.com). But that was enough to lead Sam to a spam site that looked the legitimate one, page by page. (This is just an example. Please note.)
He was close to typing in his credentials to access his account when he realized something was off about the site. Because Sam had bought CLB and had the appropriate amount of CLB to use Cloudbric’s services, he was able to utilize the Secure Web Gateway and CLB wallet when he opened an account with Cloudbric.
Sam can also earn CLB in this use case example. After visiting the malicious site, an attack log was generated. Sam chooses to share this attack log with Cloudbric and in the process receives CLB tokens as compensation.
Sam learns that the more devices the registers or the longer he uses Cloudbric’s services the more CLB he can earn, so he decides to register his PC and tablet too.
Now that he’s being protected from all kinds of cyber threats by Cloudbric, Sam feels at ease when exchanging crypto.
Check out our infographic below for a quick summary!