According to The Federal Reserve, card fraud losses on any type of USA card total up to $ ...
What Is Zero-Day Attack?
Zero day attack leave vendors desperate for a fix Zero-day attack, as cool as it may sound, is o ...
The Danger of Online Identity Theft and Protection Against It
Hackers will steal your identity and information whenever possible Identity theft is one of the ...
Manage Risk and Growth with Small Businesses – National Small Business Week
An extremely large influence for sustaining economic growth and encouraging creative problem solving ...
Security in IoT
IoT is transforming the way our society tracks and evaluates information while also transforming th ...
How to Effectively Protect Sensitive Data Stored in The Cloud
The cloud can be a vulnerable place It’s pretty clear by now that the next frontier for on ...
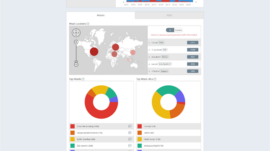
User Feedback Means New Console and Better Results
Today, Cloudbric has launched the upgraded Console 2.0. Cloudbric has received tons of precious cust ...
SQL Injection: What Is It and How to Protect Yourself?
SQL Injection attacks can manipulate data or code SQL (Structured Query Language) is a programmi ...
Can Cloudbric Protect Me From Malware?
Malware can approach your website in many different ways. Lately we've been receiving a lot of q ...