According to a survey that was conducted by The Identity Theft Resource Center, the number of data l ...
Ransom DDoS: “Give us Bitcoin or we will attack you”
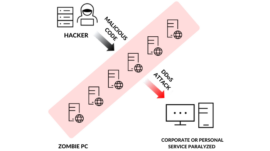
Hackers are always finding new ways to transform traditional attacks to make a more effective and po ...
Virtual Private Networks (VPN): Is There a Downside?
Since the dawn of the internet, our privacy has been at risk. To paraphrase The Police—a h ...
Year in Review: Top DDoS Attacks In 2020
Since the COVID-19 pandemic started spreading across the world in the first quarter of 2020, a l ...
7 Tips on How to Recover From a Ransomware Attack
This guide will discuss the steps you can take to retrieve your data from a ransomware attack su ...
DDoS Extortion Campaigns (Ransom DDoS, or RDoS) To Watch Out For
A ransom-driven DDoS attack is a new scheme performed by a group of cybercriminals that threaten to ...
WAF and DDoS Protection: A Must-Have for Managed Security Services Providers (MSSP)
Web Application Firewalls (WAF) are one of the most important security technologies against deni ...
What is cloud security? Can users keep the cloud 100% safe with the help of a WAF?
IT security is more than just managing a single server. Now, the growing popularity of the cloud ...
9 Tips To Protect Your Business From DDoS Attacks
DDoS attacks are among the most complex and devastating cybersecurity threats that organizations ...
PoC For The Cloud WAF (Web Application Firewall)?
What is PoC?PoC refers to Proof of Concept (or PoC) and is used in almost all industries as a way fo ...