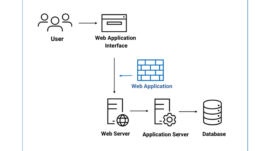
Web security was a hot topic in the news over the last few years with hackers targeting big industri ...
Multi-cloud for the Remote Environment
Nowadays, we are all getting used to the remote environment, where work, school, and shopping are mo ...
Hardware, Software, and Cloud Web Application Firewall
Depending on your business environment and purpose, you can build a more effective security system b ...
A Closer Look at 3 Major Aspects of The Future of Cybersecurity
Cybersecurity is a field in high demand. With the modern shift to virtual systems and work proce ...
3 Ways to Minimize Data Exposure When Surfing the Web
Smartphones, laptops, smartwatches, and other various IoT devices available and used by people has l ...
Five Ways to Keep Your Website Safe from Bots
Did you know that more than half of the traffic on the Internet are bots? Bots can play a benefi ...
Difference between a Public Cloud and a Private Cloud
According to the U.S. National Institute of Standards and Technology (NIST), cloud computing is ...
COVID-19 Toolbox Checkup: Meeting New Data Security Risks
The global pandemic has brought both tragedy and unprecedented change in our personal lives.&nbs ...
How Much Will a DDoS Attack Cost Your Business?
There’s no doubt that DDoS attacks are becoming more frequent and sophisticated. Cybercrim ...
The Rise of Artificial Intelligence (AI) DDoS Attacks
“Automation might be a good thing, but don’t forget that it began with Frankenstein.” — Anonymous. ...