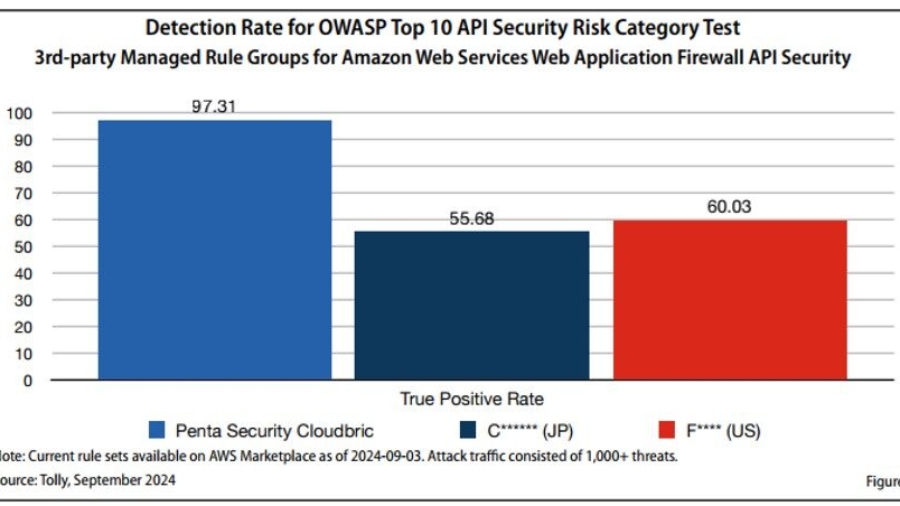
Not a Web Application Firewall expert? No worries – you’re not alone, and frankly, you shouldn’t have to be. There was a time when deploying AWS WAF (Web Application Firewall) meant diving into a sea of custom rule configuration, learning the arcane art of regex patterns and attack signatures like a true WAF guru. But times have changed. Thanks to managed rules for AWS WAF, e ...
Elevate Your AWS Security with Cloudbric WMS: The Ultimate WAF Managed Service for Effective WAF Management
Introduction In today’s ever-changing digital landscape, robust security management is a must for any business operating online. With cyber threats evolving rapidly, companies need efficient solutions that not only defend against attacks but also maintain service stability. This is where Cloudbric WMS comes into play. Cloudbric WMS (PAYG) streamlines web application firewall managem ...
10 Signs Your Website Might Be Vulnerable to Malicious IP Attacks
In today’s fast-paced digital world, web security is no longer optional—it’s a critical component of online success. With data breaches and cyber threats on the rise, securing your website from malicious IP attacks is more important than ever. One of the most powerful tools at your disposal is AWS WAF (Web Application Firewall). By leveraging managed rules for AWS WAF, you ca ...
From AirDrop to Alexa: Exposing the Hidden Trails of Your Digital Footprint
Tech in 2025 is all about convenience—quick file transfers, instant messaging, and voice assistants. But have you ever stopped to think about how much personal data you’re sharing? From AirDrop to Alexa, bits of your identity can leak online more easily than you might realize. The AirDrop Hack That Shocked Users AirDrop makes sharing files a breeze, but hackers fo ...
“Vulnerable APIs and Bot Attacks: Mitigating the Growing Costs of Insecure Endpoints”
"Vulnerable APIs and Bot Attacks: Mitigating the Growing Costs of Insecure Endpoints" Introduction In today’s hyperconnected world, APIs are the backbone of digital ecosystems, enabling seamless integration between applications and systems. However, the convenience of APIs comes with significant risks. According to a recent report by The Hacker News, vulnerable AP ...
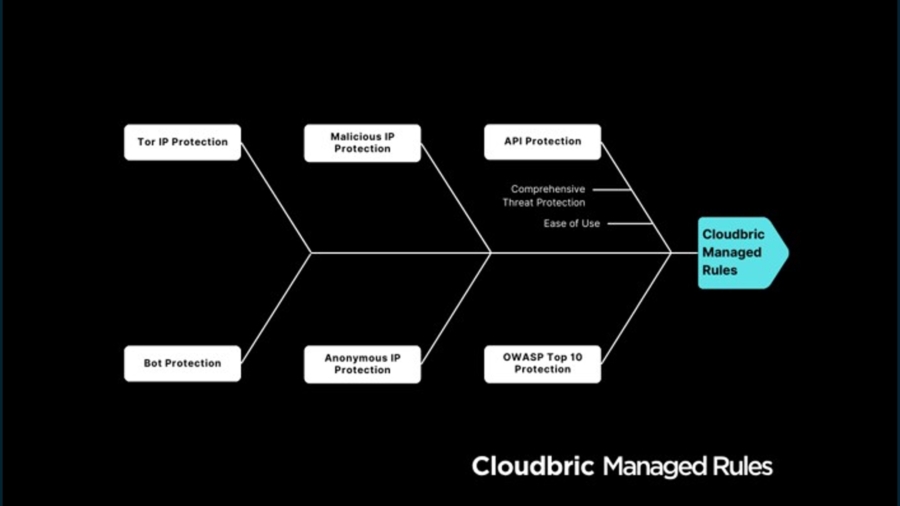
Next-Level Protection against Malicious IPs with Cloudbric Managed Rules
Next-Level Protection against Malicious IPs with Cloudbric Managed Rules In the rapidly evolving digital landscape driven by the rise of digital transformation (DX), companies are increasingly shifting their business and operations to be more software-centric. This shift has brought application development to the forefront, making robust cybersecurity—esp ...
How Cloudbric VPN Protects Your Privacy and Data on Public Wi-Fi
How Cloudbric VPN Protects Your Privacy and Data on Public Wi-Fi Do you want to surf the internet anonymously and protect your data and identity at all times? If yes, you need a VPN service that provides end-to-end encryption and anonymous usage. In this article, we will understand what a VPN is, how Cloudbric protects your privacy, and why you ...
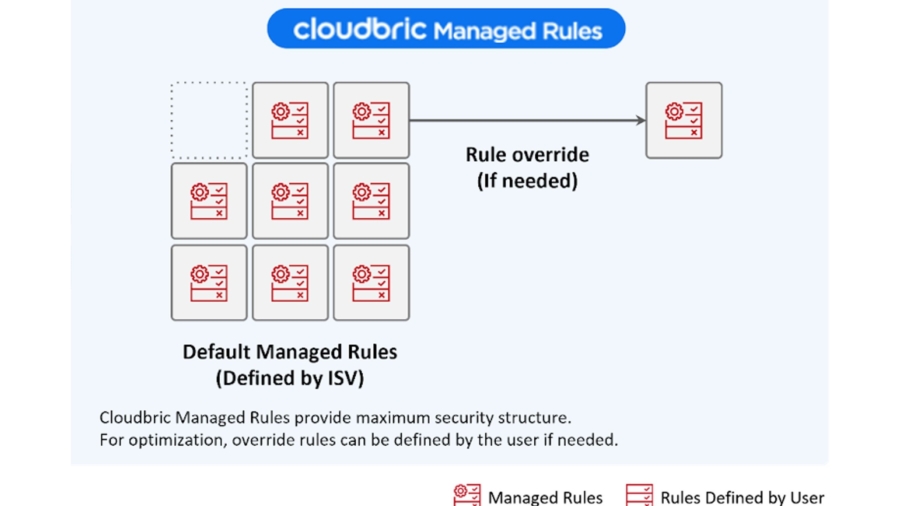
How to Utilize Cloudbric Managed Rules to Its Maximum Potential
How to Utilize Cloudbric Managed Rules to Its Maximum Potential AWS WAF, according to AWS, is a web application firewall (WAF) that helps protect web applications from attacks by allowing you to configure rules that allow, block, or monitor (count) web requests based on conditions that you define, such as IP addresses, HTTP headers, HTTP body, URI strings, SQL injection, and c ...
APIs are Everywhere. Are You Protected from API Attacks?
APIs are Everywhere. Are You Protected from API Attacks? API security has become a major focus in cybersecurity in recent years. The global research firm, Gartner recognized the importance of API security and proposed a new model of web application security, which they named Web Application and API Security (WAAP). API, which stands for Application Programming Interface, is a ...
Anonymous IP: Why You Should Block It and How.
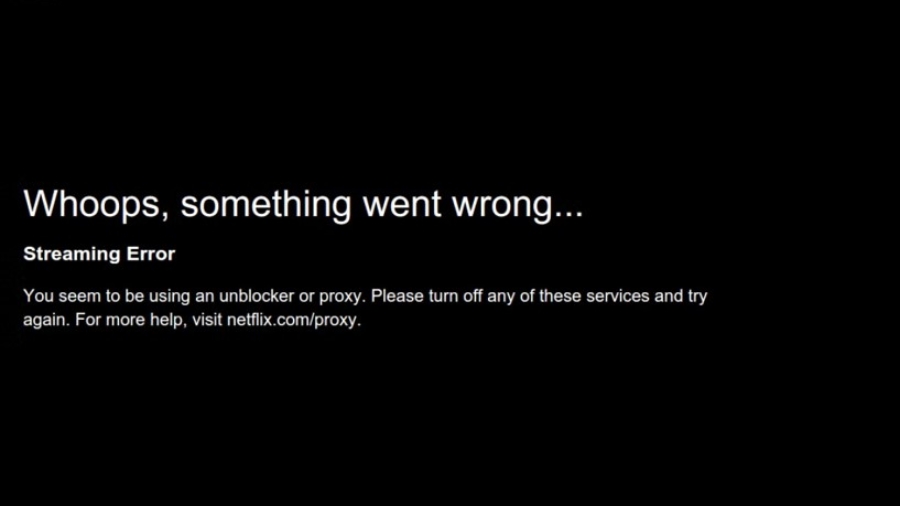
Anonymous IP: Why You Should Block It and How. In February 2016, the global content streaming service, Netflix, officially announced that it would block all VPNs and proxy use on its platform. This decision came as a response to the abuse of Anonymous IPs, which had been a persistent issue for the service. Although many users would employ Anonymous IPs for privacy and ...