Data Privacy Day is an international effort held annually on January 28th to promote the protection of personal information online. The National Cyber Security Alliance (NCSA) has assumed leadership of this effort starting in August 2011. The NCSA is aided by select DPD Champions, a fleet of enterprises, educational institutions, nonprofits, and government organizations co ...
Why Your Small Business Needs a Web Application Firewall
In the United States, small businesses account for 75% of registered businesses in the country. With over 28 million small businesses, Americans are becoming braver and many are launching businesses for themselves. These businesses are often independent—funding everything completely themselves. And as the world becomes more and more digitalized, within those 28 million businesses, ...
How Cloudbric Prevents Data Leakage: Private Information Protection
With this article, we are continuing the series: How Cloudbric Prevents Data Leakage with a focus on identity protection. In 2014, total cases of identity theft in the United States alone reached 18,000,000-- 37% over 2013. Hackers can program backdoors in your web app. As we shared in our How Cloudbric Prevents Data Leakage: Parameter Tampering article, most data breaches are cau ...
How to Block Spam Bots from Your Analytics and Website
Anyone with a website and a comments section knows the feeling of excitement followed by dread when seeing spam comments. If you have set up your Google Analytics or other analytics tool to include page comments tracking, you will be able to track the number and rate at which users comment on your website. If you see your comment numbers skyrocket, you get excited. You may think, “ ...
For CMS Security, Drupal is the Clear Winner
Drupal offers robust website security The Content Management System (CMS) market is a very competitive sector. There are many key players involved that are vying for user attention. Each CMS provider offers unique features and performance that cater to various audiences. For instance, WordPress, one of the largest CMS players in the world, powers a disproportionate amount of websites ...
Are You Protecting Against Internal Data Breaches?
When prompted with the word “hacking,” often times, people’s first thought is of a guy sitting in the dark on his laptop trying to access a company’s server hundreds of miles away. However, according to Infosecurity Europe, 42% of security professionals consider hack attacks to come from day-to-day activities like insider threats. Although the media often ta ...
Is WordPress Safe to Use For My Online Business?
WordPress is the most popular CMS If you’ve ever built a website or own an online business, there’s a good chance that you’ve heard of WordPress. WordPress is the most famous website building Content Management System (CMS) in the world today. Not only is it the most famous, but it is also the most widely used CMS in the world. VentureBeat recently announced that Wo ...
How Cloudbric Prevents Data Leakage: Parameter Tampering
Parameter tampering can manipulate web applications As we all know, many data breaches are caused by web attacks. A large majority of web attacks aim to access or send unauthorized requests to a web server in order to disclose outgoing sensitive data coming from the web server. To protect against these attacks, Cloudbric works hard to not only monitor incoming website traffic, but to ...
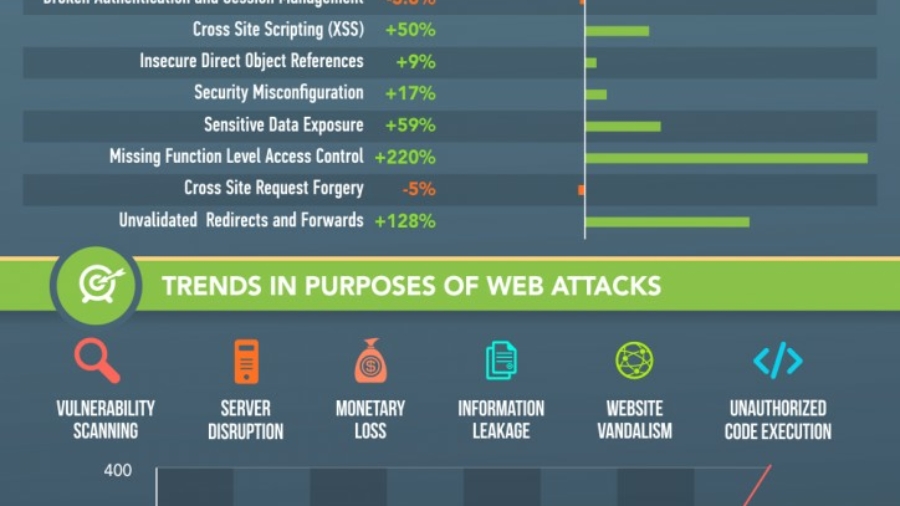
2015 Web Attack Trends Infographic
Check out our latest infographic for web attack trends for the first half of 2015. This data is based on WAPPLES (Penta Security's hardware WAF appliance) and Cloudbric (Cloud WAF) customer web traffic data from January to June 2015. All customers consented to the collection and dissemination of web attack data. Web Attack Infographic Look for the latest news in cyberse ...
Does your WAF Service Have a Low False Positive Rate?
As cybersecurity threats continue to increase, corporations’ cybersecurity budgets continue to grow. In recent years, in order to protect their cyber assets, companies have started investing in strong programming talent, robust cybersecurity internal protocols and even higher physical security in their facilities. However, when companies come to the decision to choose a protection ...