Rarely do things come easy within the business world, especially within the information security sector. Various misconceptions are often made concerning best practices when approaching information security, but hopefully this article can help clear some things up in order to help small/large business pursue cyber protection efficiently and become more familiar with IT structure. Inform ...
Cloudbric Selected as a Finalist for The SC Magazine Awards
On June 7th, SC Magazine will announce the winners for this year's SC Magazine Awards. SC Magazine announces Penta Security Systems Inc. (Cloudbric’s parent company) as one of seven finalists for this year’s SC Magazine Europe Awards highlighting outstanding leadership within the information security industry. Cloudbric has also been recognized as one of five finali ...
Which Industry Is Most Vulnerable To Hacks?
The Dark Web is a hacker's playground. Previously, we discussed the different industries that are targeted for DDoS attacks. Below, we'll begin by pointing out some interesting industry facts and then look at some examples of how hackers like to get creative with their revenue strategies. Which Industry Is Most Vulnerable To Hacks? Research performed by a Korean media com ...
How Does Cloudbric Hide Your IP Address?
If you have a website or have interest in owning a website, you might have heard about an IP address one time in your life. Simply, the IP address means that Internet Protocol Address, which is a numerical label that indicates where your website is located. Recently, people have been easily able to discover your original IP address just by typing a one-line code or using a free softwa ...
Cyber Defense Magazine Honors WAPPLES
As you may well know, Cloudbric detection technology is based on WAPPLES, the hardware based Web Application Firewall (WAF) product by Penta Security. WAPPLES is known as an intelligent WAF that specializes in minimizing four types of web risks—web hacking, data leakage, malicious access and web defacement. Penta Security was recently honored as the Hot Company in Web Applicatio ...
4 Common Web Vulnerabilities Expected to Surface in 2016
Common Web Vulnerabilities in 2016 Many of the cyber-crimes that have been highlighted in the past few years were made possible due to common web vulnerabilities. Adversaries are finding it easy to pinpoint flaws in web pages, making it trivial for even novice hackers to exploit them. In this post, you’ll learn about four of the most common web vulnerabilities in websit ...
Website Security 101: How Hackers Hack
Did you ever wonder how hackers actually hack a website? We often hear in the news that a website was hacked—ending up with millions of customers’ personal data being compromised and often times ending up with identity theft. However, how exactly do hackers steal all that precious customer information? In order to properly hack, hackers understand how the website is b ...
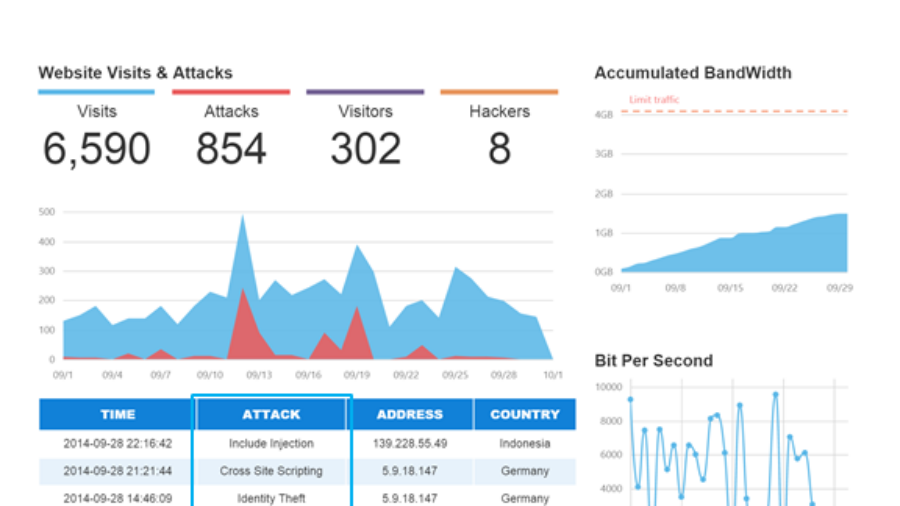
What Are The Attacks I See on My Cloudbric Dashboard?
If you log into your own Cloudbric dashboard, you can see which types of attacks attempted to attack your website by month. Just filter the dates that you want to analyze, and you can see your total website visits compared to the attempted hack attacks. In the below example, you can see that this month, there were a variety of hack attacks attacking this website (Include Injection, Cr ...
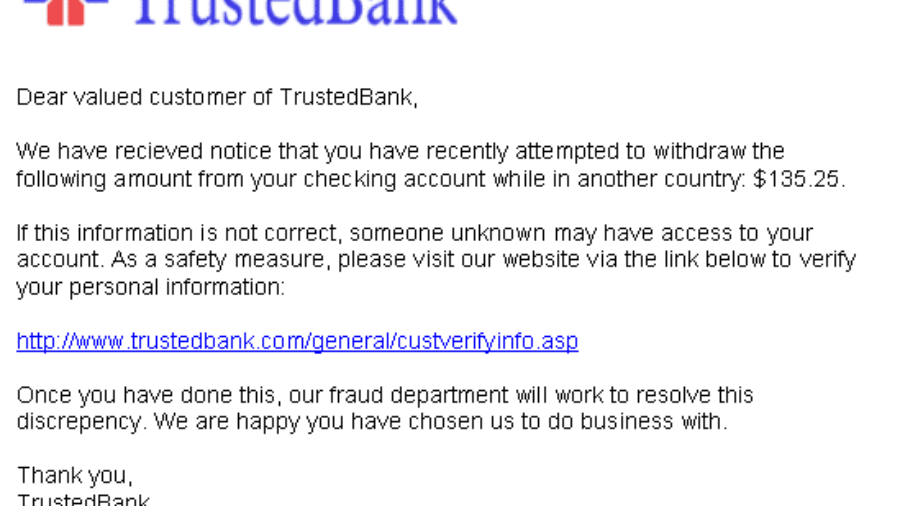
How Does Cloudbric Protect Against Phishing Websites?
Almost everyone has received a questionable e-mail from a seemingly reliable source. Perhaps, the e-mail looked like it was from your bank because it detected fraudulent activity on your credit card. However, upon further inspection, you noticed that the actual e-mail address and its language looked a bit different than usual. At that moment, you probably realized that it is actually ...
Website Defacement: Suspicious Changes On Your Website
Imagine—you have finally moved into your dream neighborhood. You have worked very hard for this moment and are excited to spend your first night in your new home. The next morning after a great night's sleep, you go outside to pick up your mail. However, you see this on the side of your house: No one wants their property defaced. Graffiti. Some delinquents outside of the ...