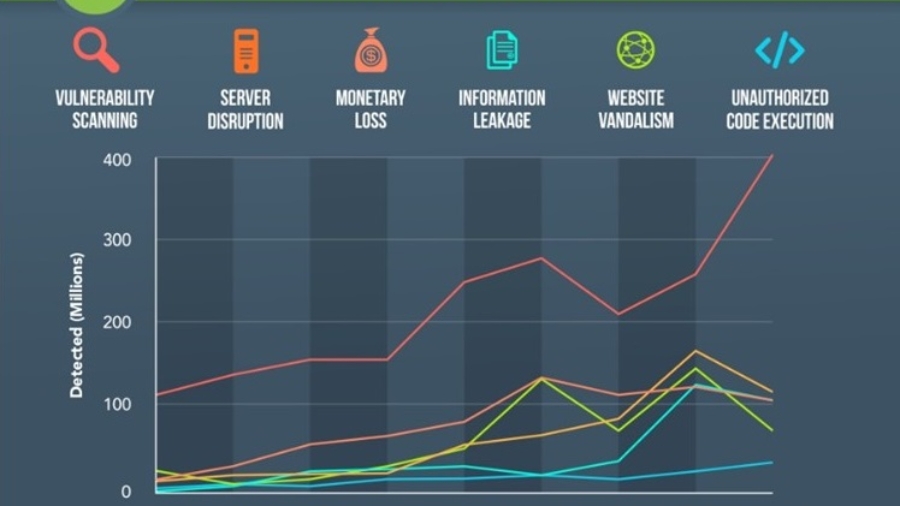
ハッカー は何の為にWebサイトをハッキングするのでしょう。 インターネットが普及されていなかった頃のハ& ...
Dealing with The Cloudbleed Aftermath: How to Quickly and Safely Switch WAF Services
While the word “cloud” has been growing in popularity and the “IT-trend” in virtual circles everywhere, the past couple of weeks have been a tough one for the Cloud. The term “Cloudbleed” has been tossed around the IT and Cloud communities as a critical security flaw in Cloudflare’s CDN was recently discovered. It is ironic how catastrophic t ...
7 Easy Ways to Protect WordPress Sites from Hackers
WordPress sites are highly targeted by hackers. There used to be a time when hacking was seen as a difficult skill that only evil coders in dark, solitary rooms could pull off. However, we’re no longer in that cyber era. Nowadays anyone can be a hacker, and most hackers can easily access and attack vulnerable websites. In fact, these days hackers can break into target systems w ...
Difference Between Phishing and Pharming
While phishing and pharming did not gain momentum until the mid-2000’s, they have been a force to be reckoned with since they first made waves on the Internet. According to a case study by Wombat Security, two-thirds of the organizations they studied have experienced targeted and personalized phishing attacks. (More chilling phishing facts here!). But phishing scams do not dis ...
Cloudbric Offers Online Safety Tips In Celebration of Safer Internet Day 2017
Cloudbric is a proud supporter of Safer Internet Day. A safe and civil Internet doesn’t depend on just you or me. It depends on all of us – that includes businesses, schools, organizations, local communities, and individuals. This year Cloudbric is a proud supporter of Safer Internet Day, an awareness-raising campaign that started in Europe more than a decade ago and is n ...
Partner Success Story: Celebrating Valued Customers with Luhost
Luhost's CEO for an in-depth interview with Cloudbric. “After using other website security services, Cloudbric is the only one that has proven to be effective, fast, reliable and flexible. For many years, I have trusted Cloudbric with all our websites. Highly recommended!” - Bryan J. Rincon CEO and President at Luhost. We view feedback as an important aspect of evaluat ...
XSS: The Con-Artist
“XSS” is an acronym you hear often in the field of information security as it’s a common attack found in web applications affecting both the client and the server. And while acronyms can fool you into thinking that it’s quite hi-tech and complicated, at the root of it, XSS is simply a con-artist, waiting for his next ploy. What is XSS? Short for Cross Site S ...
Website Building: Speed vs Security
Do you remember the story of The Three Little Pigs? The first two pigs were almost killed by the big bad wolf because they were lazy and chose to build their houses with either straws or sticks. Their houses seemed stable at first, but in reality, were too weak to protect them against an outside attacker. It was only the third pig who was safe because he chose to build his house with bri ...
A Year in Review: The Top Ten Cyber Attacks of 2016 in The Gaming Industry
Political parties and figures, international banks, and big hosting corporations were not the only ones subject to cyber attacks this past year. Hackers also set their eyes on the gaming and entertainment industry by carrying out massive attacks year-round. In fact, a security report by Akamai revealed that more than half of the DDoS attacks during the first quarter were targeted at ...
Interview with SYS-CON TV at Cloud Expo: The Current State of Cloud Security
https://www.youtube.com/watch?v=Nq-0wNrf0FY SYS-CON Media has been connecting technology companies and customers through a comprehensive content stream covering a myriad of subject areas including cloud computing and web security through various events for over two decades now. Cloud Expo is among their international recognized brands, and this year the 1 ...