Can you really track a DDoS attack? Would you be able to find who's behind the attack? Who’s DDoSing you? The first “D” in the compound word “DDoS” is the big problem. Tracking a “Distributed” attack coming from thousands of infected machines turned into bots is no easy task. But using a detective’s most popular tools, like back-engineer ...
10 DDoS Attack Trends To Watch Out For In 2021
A distributed denial of service (DDoS) attack often involves multiple computer systems or bots flooding a target system with illegitimate traffic. The target server becomes overwhelmed and either stop functioning or malfunctions when legit traffic (i.e. visitors) comes in, resulting in disruption of core business operations. In recent years, DDoS attacks have become a common ...
10 Important Web Application Security Trends You Need To Know
Cybercrimes are the biggest threat to every online company globally, with a web attack occurring once every 39 seconds. To make matters worse, traditional firewalls and antivirus software could be irrelevant in preventing these attacks and possible breaches. Application security goes a long way in ensuring your applications are secure by finding, fixing, and enhancing the security ...
A Fully Managed WAF Benefits
There is no autopilot on a Web Application Firewall (WAF). An automatic turn/off button that sets your WAF to do all the work while you forget about security. If you don't want to risk DDoS, XSS, SQL injection attacks, you will have to grab the manual control and start deploying, configuring, and operating your WAF. But this is no task for the ordinary web admin. Depending on th ...
Web Application Firewall (WAF) Buyer Guide: Checklist for Evaluating WAFs
A Web Application Firewall (WAF) can protect your web applications and website from the many intrusions and attacks that your network firewall cannot. Depending on its type, a WAF can protect against buffer overflows, XSS attacks, session hijacking, and SQL injection. However, not all WAFs are equal, and definitely, they do not provide the same level of security. Here is a checkli ...
10 Cons When Using Open-Source Web Application Firewalls
A Web Application Firewall (WAF) is a firewall meant for HTTP applications to prevent cyberattacks such as cookie-poisoning, cross-site forgery, cross-site scripting, SQL injection, and file inclusion. There are both commercial WAFs and open-source WAFs. Commercial WAFs are expensive and not always affordable. Open-source WAFs exist to create accessibility to WAF technology ...
Types of Cloud WAFs (Web Application Firewall Services)
Web Application Firewalls (WAFs) were initially built to protect web applications. That includes all of its underlying resources, from servers, databases, networks, etc. To accomplish this, the WAF monitors the traffic between the app and the client and filters out (or blocks) unwanted or suspicious traffic based on a set of rules. WAFs are a critical element in any web defense ...
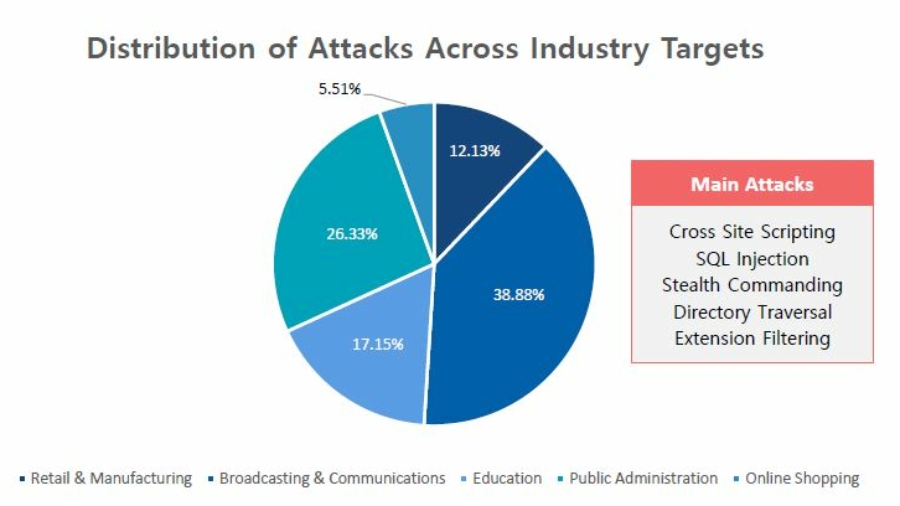
Cloudbric and Penta Security Systems Releases Annual WATT (Web Application Threat Trend) Report
The Web Application Threat Trend Report (WATT report) is an annual report, complied with the log data from Penta Security’s WAPPLES, and Cloudbric’s cloud-based WAF (Web Application Firewall). This report only contains data that customers have agreed to share. The main purpose of this report is to find out possible future web attack patterns through the l ...
What is the importance of HTTP and HTTPS?
Have you ever noticed that something appears at the front of every website link? That is either HTTP or HTTPS. But even when you type in the website address without the HTTP or HTTPS, you are still directed to that particular site. So what do an HTTP and HTTPS do? Reading our blog on our official blog page is one example. So when you click on one of our blogs the data that appears o ...
5 Data Leakages That Shook Up 2020
According to a survey that was conducted by The Identity Theft Resource Center, the number of data leakages has declined in the first half of 2020 and the number of victims has decreased by 66% compared to last year. But you should not let your guard down just because the number of cases has gone down. The pandemic that began this year has led to a surge in the use of remote acc ...