APIs are Everywhere. Are You Protected from API Attacks?
API security has become a major focus in cybersecurity in recent years. The global research firm, Gartner recognized the importance of API security and proposed a new model of web application security, which they named Web Application and API Security (WAAP). API, which stands for Application Programming Interface, is a mechanism that enables two software components to communicate with each other using a set of definitions and protocols. APIs are generally used to provide access to data and services, allowing the developers to build new applications and tools by leveraging existing data and functionality.
For instance, if a new food delivery app requires a map to display local restaurants, it would be inefficient for the developers to create a new map and gather all the restaurant data themselves. Instead, they could use an existing map API, such as Google Maps, to retrieve the necessary data for their app.
APIs are becoming indispensable in modern software development because of its;
- Interoperability
- APIs facilitate interoperability between software systems, and by using APIs, applications and services developed by different developers would work together, share data, and provide integrated solutions
- Modular Development
- APIs allow complex systems to be divided into smaller and more manageable components, making software development, testing, and maintenance easier. Developers can focus on building and updating specific functionalities.
- Cross-Platform Integration
- APIs enable cross-platform integration, allowing applications to work across different devices and environments.
- Data Access and Sharing
- APIs define a structured way for data to be exchanged between applications, usually formatted in JavaScript Object Notation (JSON) or Extensible Markup Language (XML). This standardization ensures that both the requesting application and the providing system can easily interpret and process the data.
Despite their benefits, not all APIs are built with security measures, and an increasing number of organizations have reported attacks targeting APIs, resulting in significant damage to their services. Such was the case with Duolingo. Duolingo is a company that services a vastly popular language learning application. It is estimated that by the end of Q1 2022, Duolingo’s monthly active users reached 49.2 million. Naturally, due to its massive volume of user data, Duolingo’s user database became a target for hackers. In January 2023, scraped data of 2.6 million Duolingo users appeared on the dark web hacking forum called “Breached.” The scraped data included email addresses, personal names, usernames, and other user profile information.
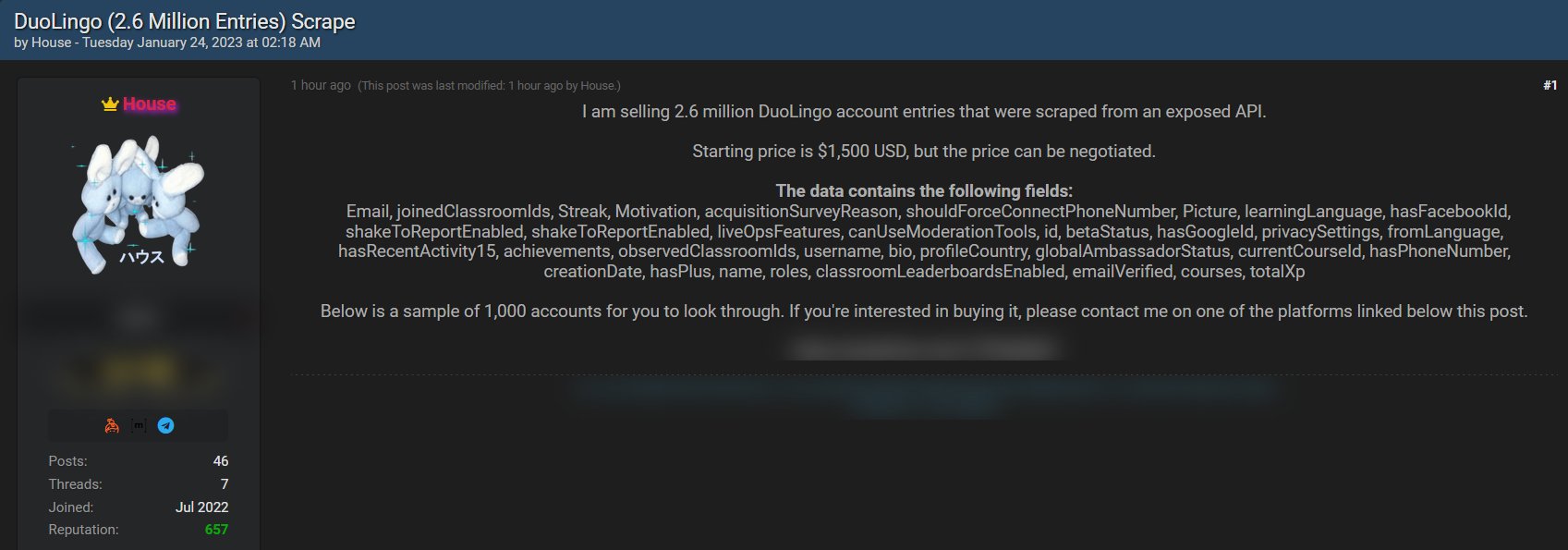 screenshot courtesy of FalconFeedsio
screenshot courtesy of FalconFeedsio
It is believed that the hacker acquired the user data by infiltrating Duolingo’s API vulnerability. Duolingo’s API provided access to user information based solely on email or username without asking for any other forms of verification. The API did not take any security measures to ensure that the requests were coming from legitimate users, thus the access to user data was not restricted. This incident would be categorized under two vulnerabilities of OWASP Top 10 API Security Risks:
- API2:2023 – Broken Authentication
- API3:2023 – Broken Object Property Level Authorization (BOLA)
As API has become a target for hackers, establishing API security became an important task for any organizations or businesses providing services that include APIs. There are already numerous solutions for API security in the market, but the important question to ask is: which of the solutions best fit my environment?
As there are a myriad of APIs for different purposes, solutions for API security can also take many different directions and approaches. For instance, some may focus on specific vulnerabilities of APIs, such as Injection attacks or Broken Authentication, while some may focus more on API Discovery. Some may even choose to focus more towards API Gateway. There is no definitive answer to what type of solution is best. Therefore, it is important that organizations and businesses carefully assess their environment and needs before adopting a solution.
Penta Security’s direction in establishing API security was to build a solution that focuses on the actual API attacks and vulnerabilities. Penta Security has recently launched a managed rule group for AWS WAF, Cloudbric Managed Rules for AWS WAF – API Protection (API Protection). Taking advantage of the characteristics of managed rule groups for AWS WAF, which enables the user to quickly adopt the security rules predefined by security vendors simply through subscribing to the product, Penta Security provides a quick and easy solution for AWS WAF users to detect and block API attacks. API Protection was created to provide security against the threats of OWASP API Security Top 10 Risk. To respond to the attacks and vulnerabilities of API, API Protection utilizes the API attack data gathered and analyzed by Penta Security’s own cyber threat intelligence (CTI) and establishes security against known API attacks. Furthermore, API Protection provides validation and protection for XML, JSON, and YAML data. API Protection was recently validated to have the highest detection rate among API Security managed rule groups currently provided in AWS Marketplace through a comparative test conducted by a third-party IT testing, validation and analysis company, The Tolly Group.
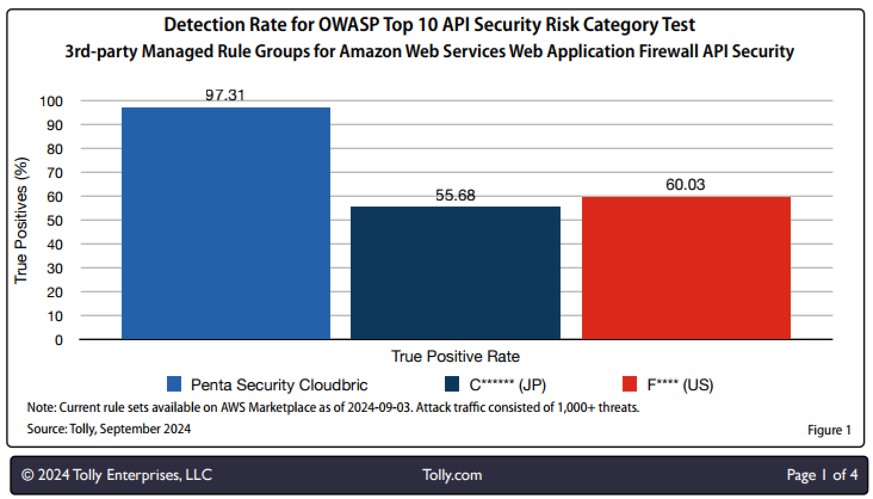
The Tolly Group – 3rd-party IT Testing, Validation, & Analysis
With a cost efficient, pay-as-you-go pricing, users are able to implement a robust API security without the need for security expertise, just by subscribing to the product.
Cloudbric Managed Rules for AWS WAF – API Protection is available at 





