Anonymous IP: Why You Should Block It and How.
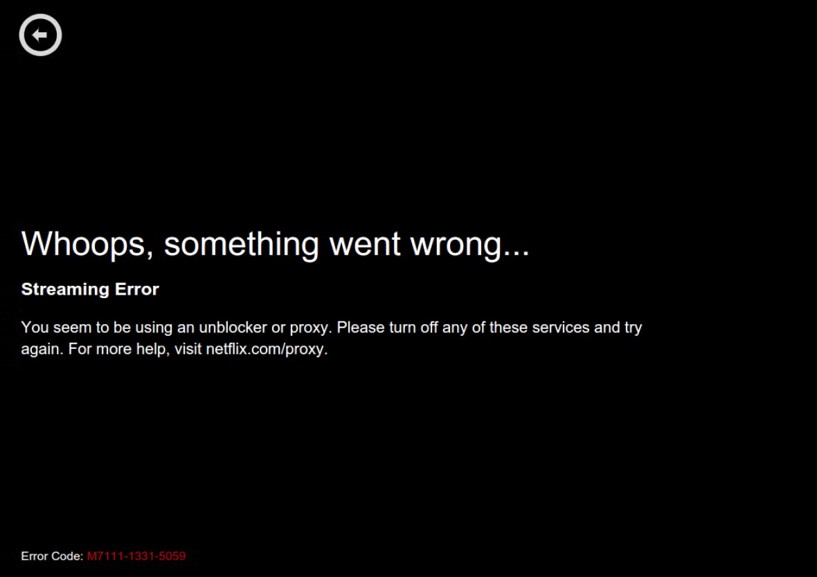
In February 2016, the global content streaming service, Netflix, officially announced that it would block all VPNs and proxy use on its platform. This decision came as a response to the abuse of Anonymous IPs, which had been a persistent issue for the service. Although many users would employ Anonymous IPs for privacy and security reasons, some exploited them for illegal purposes. One example was Netflix users using VPNs to bypass the geo-restrictions on contents that are not available in their region. The geo-restrictions were put in place due to licensing agreements, but users soon discovered that accessing the platform through an IP from another country allowed them to stream the geo-restricted content. As a result, Netflix was forced to address the issues related to license and copyright infringement.
Anonymous IP utilizes methods such as VPNs, Tor Nodes, Proxies, and Data Centers to mask the IPs and the geolocation to protect the privacy of the user and provide a secure access to the web. However, it is also a double-edged sword that can very well be used for illegal activities such as:
As such, detecting and blocking Anonymous IPs can be a smart move for companies and organizations of all industries to reduce the risk of cyber threats.
Many companies and organizations already make use of various solutions to respond to Anonymous IPs. Like Netflix, a significant number of content streaming services and other companies in the media & entertainment industry have adopted Anonymous IP-related solutions to protect their media contents. Some companies use Anonymous IP-related solutions to prevent DDoS attacks carried out by zombie PCs infected via Data Centers. Online game companies block illegal access to geo-blocked servers, and finance companies, including cryptocurrency platforms, prevent fraud by blocking attempts to bypass the geolocation restrictions.
Such solutions are largely categorized into two types: IP Reputation Database (often referred to as “IP Reputation Checkers”) and IP Reputation Filters. There are pros and cons to both types of solutions, and the choice between them depends on the available resources and the needs of the user.
| IP Reputation Database | IP Reputation Filters |
|
|
|
Penta Security’s direction in responding to Anonymous IPs is IP Reputation Filters. Penta Security currently provides a managed rule group, Cloudbric Managed Rules for AWS WAF – Anonymous IP Protection, in the AWS Marketplace.
Taking advantage of the characteristics of managed rule groups for AWS WAF, which enables the user to quickly adopt the security rules predefined by security vendors simply through subscribing to the product, Penta Security provides a quick and easy solution for AWS WAF users to detect and block any threats that can be caused by Anonymous IPs. Penta Security’s Cloudbric Managed Rules for AWS WAF – Anonymous IP Protection is defined based on the Anonymous IP List, which is continuously updated with the latest IP Reputation data, collected and analyzed by Penta Security’s own Cyber Threat Intelligence (CTI). With a cost efficient, pay-as-you-go pricing, users are able to implement a robust security solution against Anonymous IPs without the need for security expertise by subscribing to the product.
Cloudbric Managed Rules for AWS WAF – Anonymous IP Protection is available at
 link.
link.




