How to Utilize Cloudbric Managed Rules to Its Maximum Potential
AWS WAF, according to AWS, is a web application firewall (WAF) that helps protect web applications from attacks by allowing you to configure rules that allow, block, or monitor (count) web requests based on conditions that you define, such as IP addresses, HTTP headers, HTTP body, URI strings, SQL injection, and cross-site scripting. While it is undoubtedly a powerful tool to establish security for your websites and web applications, it requires users to have a certain level of security expertise to utilize the service to its fullest potential.
When the user first adopts AWS WAF, the user is responsible for implementing the security rules¹ for AWS WAF. AWS WAF provides the user with options to either create their own rules or adopt managed rule groups².
Without the proper security rule configurations, AWS WAF cannot function or operate properly. Consequently, the users would have to have some level of understanding of how security rules work and what kind of security rules they need.
- Security Rules : Statements that define the conditions on how to inspect the HTTP/HTTPS web traffic, or requests, made to the web applications. If the request matches the conditions, it is met with the rule action, such as Allow, Block, and Count, that is configured for the security rule.
- Managed Rule Groups : A preset of security rules created by AWS and the Independent Software Vendors (ISV) for the users.
What are Cloudbric Managed Rules?
One such example of managed rule groups that the users can implement for AWS WAF is “Cloudbric Managed Rules.” Cloudbric Managed Rules (CMR) is a managed rule group product provided by Penta Security.
CMR was created based on the security technologies and expertise of Penta Security’s WAF product, WAPPLES, which has protected web services for various organizations and enterprises since 2005. CMR utilizes Penta Security’s own Cyber Threat Intelligence (CTI), Cloudbric Labs, to provide a safer online environment for AWS WAF users.
Penta Security is not only one of the seven ISVs worldwide that offers managed rule groups for AWS WAF but also the only ISV to enable the Web Application and API Protection (WAAP) model by integrating managed rule groups with AWS WAF. There are a total of 6 different CMR rule groups currently provided in AWS Marketplace, which are able to be implemented on the AWS WAF simply by subscribing to the product.
Cloudbric Managed Rules for AWS WAF Product List
| OWASP Top 10 Rule Set
Provides security against threats from OWASP Top 10 Web Application Security Risks, such as SQL Injection and Cross-Site Scripting (XSS) utilizing the logic-based detection engine recognized by world-renowned research organizations such as Gartner and Frost & Sullivan. |
Malicious IP Protection
Provides security against malicious IP traffic based on the Malicious IP Reputation list created using ThreatDB, which is collected and analyzed from 700,000 websites in 148 countries worldwide by Cloudbric Labs, Penta Security’s own Cyber Threat Intelligence (CTI). |
| API Protection
Provides security against the OWASP API Security Top 10 Risk by establishing a defense system against known API attacks and providing validation and protection for XML, JSON, and YAML data. |
Bot Protection
Provides security against malicious bots, such as scrapers, scanners, and crawlers, which negatively impact and damage websites and web applications through repetitive behavior, based on the malicious bot patterns collected and analyzed by Penta Security. |
| Anonymous IP Protection
Provides integrated security against Anonymous IPs originating from various sources including VPNs, Data Centers, DNS Proxies, Tor Networks, Relays, and P2P Networks, responding to threats such as geo-location frauds, DDoS, and license and copyright infringement. |
Tor IP Protection
Provides security against Anonymous IP traffic, specifically originating from the Tor network, which can be difficult to detect using an ordinary IP Risk Index, utilizing the Tor IP list managed and updated by Cloudbric Labs. |
CMR is continuously updated and managed by the security experts of Penta Security to respond to the latest security threats and maintain a stable security level, boosting the AWS WAF experience for the users.
CMR has also recently been validated to have the highest detection rate through a comparative test conducted by a 3rd party IT testing, validation, and analysis company, The Tolly Group.
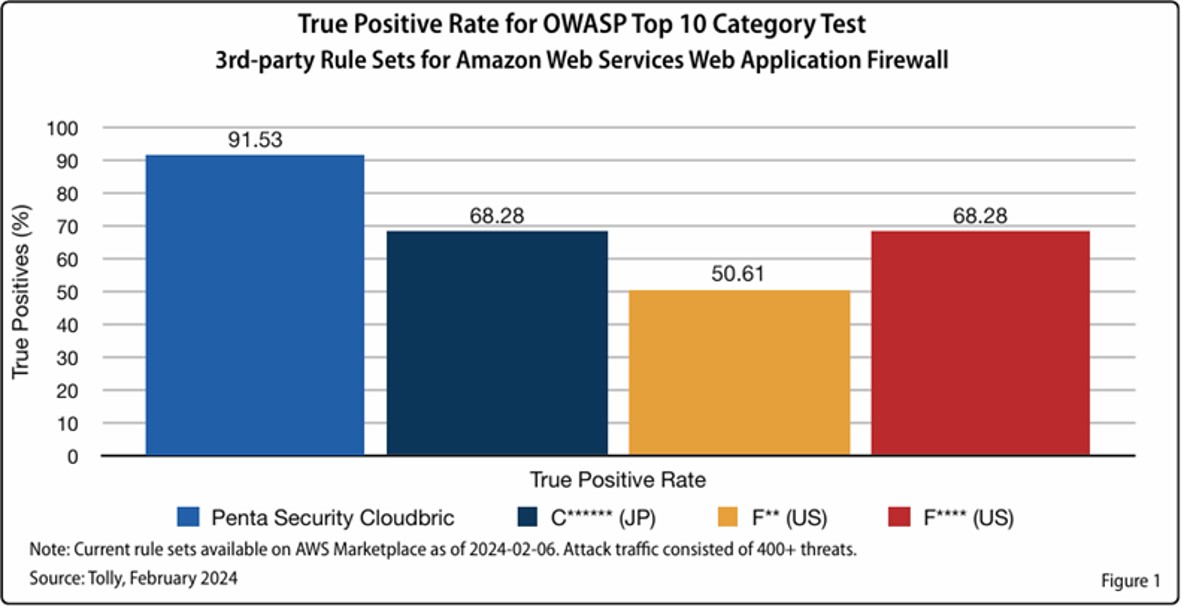
[Comparative Test Results for OWASP Top 10 Rule Set]
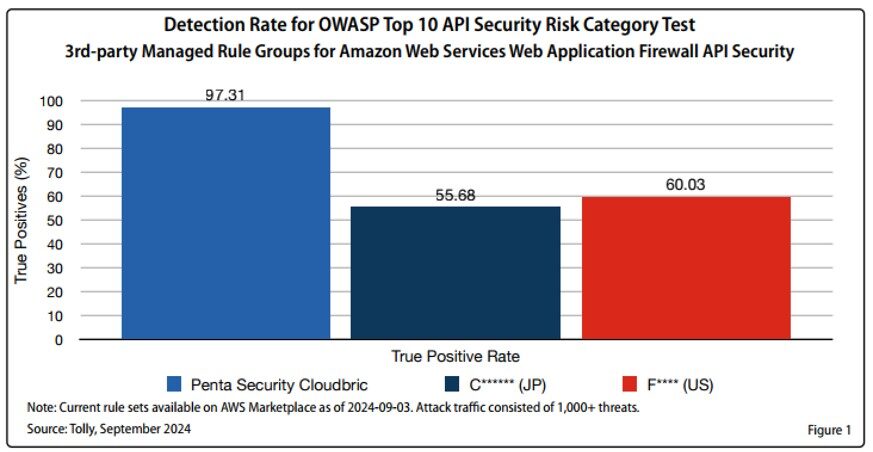
[Comparative Test Results for API Protection]
Optimizing Cloudbric Managed Rules to your environment
Managed rule groups for AWS WAF are designed to provide the users with a basic setup for security and allow the users to add conditions, such as IPs, specific headers, or regions, by creating additional rules when a new threat is identified. This is known as the Blocklist method (also known as Blacklist method). Blocklist method is widely preferred for managed rule groups as it can reduce false positives, but ultimately, the users would have to continue to add more and more rules as they progress, only after the threat or attack has occurred. CMR also utilizes the Blocklist method, but to minimize the burden of adding the rules for the users, CMR provides managed rule groups with maximum security configurations. CMR is continuously updated with the most recent Cyber Threat Intelligence to respond to new threats and vulnerabilities. In doing so, CMR can detect and block more potential threats and attacks compared to any managed rule groups provided in AWS Marketplace, and if a false positive occurs, the users would simply need to override the rule that responded to the legitimate request, instead of having to create a new rule to respond to the new malicious request. Overriding a rule can simply be achieved by clicking a few buttons, and this method can provide more stable security.
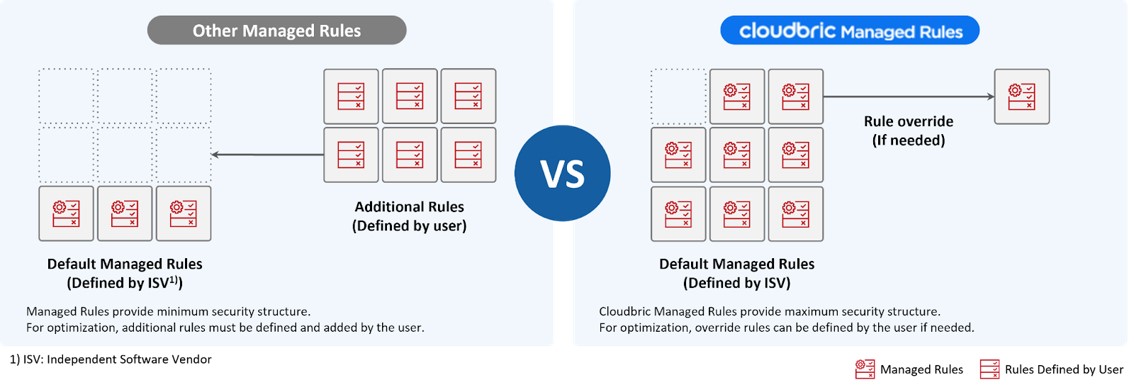
To determine whether a request should be overridden or remain blocked, it is important to analyze your detection logs. Each rule within the managed rule group is defined with a rule action that responds to the request when it matches the condition of the rule. These rule actions include “Allow,” “Block,” and “Count.” Also, the users can adjust the priority of the rule, and the request will pass through the rules in the order of highest priority to the lowest.
If the rule action defined for the rule is Allow, the request will pass through the rule, even if the request matches the conditions defined in the statement of the rule. The request will also not be logged. Allowing a rule will have all the subsequent rules to allow the request as well, so if you want a certain rule to allow the request, it is recommended that the rule is configured to have the lowest priority, as it will minimize the effect it has on the other rules. If the rule action defined for the rule is Block, the request will not pass through the rule, if the request matches the conditions defined in the statement of the rule. The request will then be logged as having been blocked. If the rule action defined for the rule is Count, the request will pass through the rule without being blocked, even if the request matches the conditions defined in the statement of the rule. However, the request will be logged.
When you decide to change the default rule actions defined for the rules, it is recommended that the rule action for the rule is first changed to Count to evaluate the impact. You must analyze your detection logs carefully while keeping your rule action to Count before deciding whether to override the rule. It is also a good idea to run your rules while having the rule action as Count when you are creating your own security rules.
From time to time, CMR will be updated with a newer version. When it is updated with a newer version, you will be notified by AWS Marketplace, and you will be given the option to update the managed rule groups to a newer version or to use the previous version. When a new version of the managed rule group is updated, the updates to the managed rule group will not be automatically applied to the product you are currently subscribed to, as updating to a newer version of managed rule groups may cause the configurations you made to the rules to revert to default state. If you wish to use the newer version of the managed rule group, you can access the AWS WAF management console to change the version of the managed rule group.
AWS WAF Management service, “Cloudbric WMS.”
While CMR was developed to facilitate the process of implementing security rules for AWS WAF, it can still be challenging if you do not have in-house personnel with security expertise. It can be quite unclear as to what threats you must watch out for or which origin IP must be blocked. Analyzing and optimizing the security rules can also be quite difficult if you do not fully understand your infrastructure and environment.
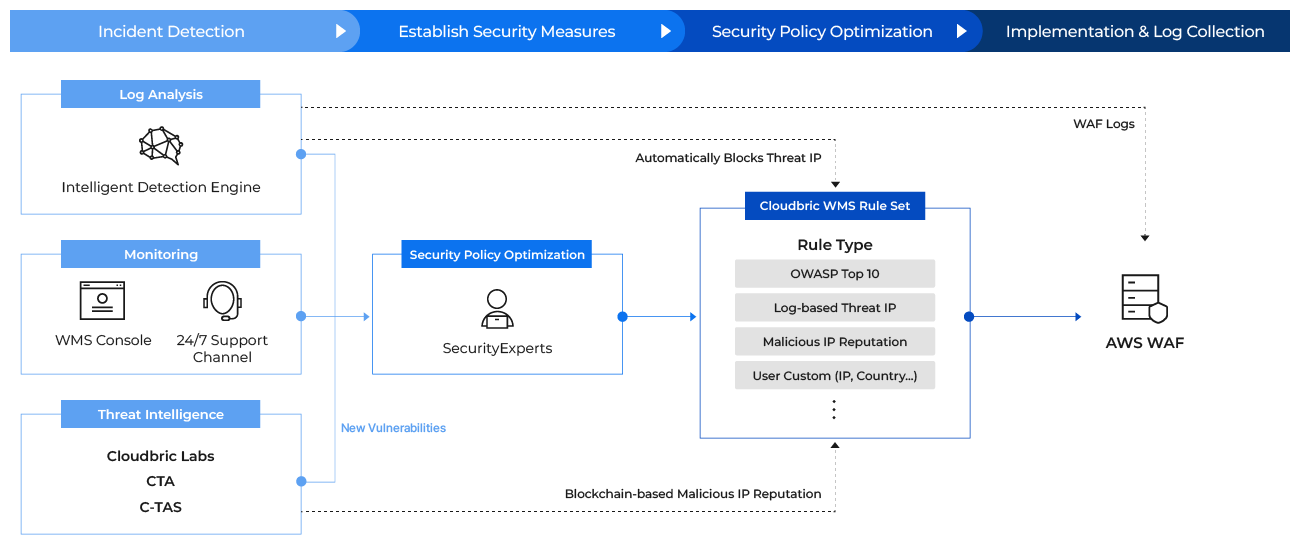
Cloudbric WMS for AWS WAF is a management service developed by Penta Security for AWS WAF users. When Cloudbric WMS is adopted, the security experts of Penta Security analyze your infrastructure and environment to adjust the conditions of the statement and optimize the rules for you. After the optimization of the security rules is completed, you are given access to Cloudbric WMS console, which provides you with an overview of your environment and security status. Cloudbric WMS enables the users to add countries or origin IPs to block through an easy-to-use GUI and provides detailed reports with all the information you need to reinforce your security.
Cloudbric WMS also offers customer support in English, Japanese, and Korean, to respond to any issues or inquiries you may have in operating your WAF.
Penta Security is an official launch partner for AWS WAF Ready, a provider partner of AWS Activate, and an AWS Public Sector Partner.
All Cloudbric Products provided in AWS Marketplace have been validated by AWS through the Foundational Technical Review.
For more information on Cloudbric WMS, please visit: 👉Cloudbric
You may also refer to the “Cloudbric Managed Rules for AWS WAF Setting Guide” for more details on how to subscribe, implement, and optimize CMR for your AWS WAF.





