Web Application Firewalls (WAFs) were initially built to protect web applications. That includes all of its underlying resources, from servers, databases, networks, etc. To accomplish this, the WAF monitors the traffic between the app and the client and filters out (or blocks) unwanted or suspicious traffic based on a set of rules.
WAFs are a critical element in any web defense strategy; as they protect your web apps from the common threats shown in the top ten OWASP’s like SQL injection, cross-site scripts (XSS), and DDoS.
Service providers offer WAFs via different deployments. For example, you can find the same WAF software via the cloud, hybrid, fully-managed, virtual machine, and even on-premises appliances, etc. In this article, we’ll focus only on the cloud-based WAF services and their different types.

Types of Cloud-based Web Application Firewall Services
Cloud-based WAFs are next-generation Web Application Firewalls. They are usually provided via the SaaS model and managed online, but they can also be supplied via fully managed services. With a cloud-based WAF, the end-user does not need any software or hardware on-premises; all the cloud-based WAF components are located in the cloud. So, users only enroll in a monthly plan and let the WAF provider take care of all underlying infrastructure and its software.
1. First-Gen WAFs
The first generation of WAFs started using the same principle of basic firewalling, blacklisting and whitelisting. These two lists provided WAFs simplicity— a binary decision; to block or to allow traffic. This approach to lists introduced a big challenge, known as false positives. Legitimate traffic would often get confused as malicious, and its access blocked. But even worse, it also introduced false negatives; potentially harmful entries would be flagged as legitimate and granted access. Sure, first-generation WAFs solved some web application security issues, but they also introduced more work to a web admin because they regularly updated the lists.
2. Signature-based WAFs
Hackers study attack patterns that worked for somebody else and try to replicate them, using the same routines and set of instructions. But whether unsuccessful or successful, attacks always leave tracks— which can be easily fingerprinted. A signature is simply a fingerprint of a known given attack (and its routines and set of instructions). Signatures can help a firewall recognize an attack on all its phases.Signature-based WAFs are considered as the second generation because they still use the whitelist/blacklist approach but enhance security with pattern management. 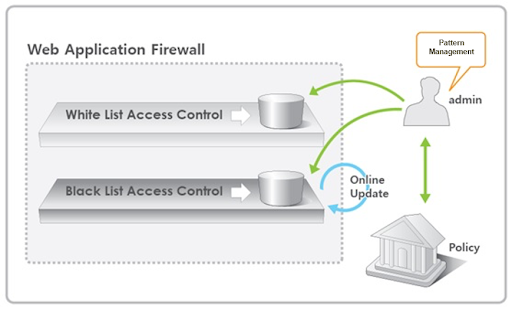 Most WAFs found in the market today run their security policies thanks to their signature lists. The WAF compares every single request and response against the signature database entries. If the WAF detects a potential attack, it issues an alert or stops it immediately. Unfortunately, anything outside the normal boundaries of an attack pattern will not be detected. Additionally, checking all traffic against the attack signature database puts a strain on the server’s performance and speed, and not checking every single packet increases the risk of false positives and false negatives.
Most WAFs found in the market today run their security policies thanks to their signature lists. The WAF compares every single request and response against the signature database entries. If the WAF detects a potential attack, it issues an alert or stops it immediately. Unfortunately, anything outside the normal boundaries of an attack pattern will not be detected. Additionally, checking all traffic against the attack signature database puts a strain on the server’s performance and speed, and not checking every single packet increases the risk of false positives and false negatives.
3. Behavior-based WAFs
Instead of using historical data (or pattern), the behavior-based WAF analyzes incoming traffic by comparing it with a specified baseline of “expected behaviors.” If a behavior deviates from the baseline, then it is an indication of a potential attack. A baseline defines what is acceptable or what is unacceptable. There are two ways to do this, either define everything as legitimate behavior, flag the rest as malicious, or vice versa, define everything as malicious and only set what is legitimate behavior. Two advantages of Behavioral-based WAFs:
- They don’t need to be updated continuously.
- They can protect assets from new and zero-day attacks.
The most noticeable disadvantage of behavioral analysis is that it is more challenging to be accurate since the attack detection coverage is lower. There is a higher risk of false positives. Cybersecurity teams can use a combination: signatures to identify known attacks and lower false positives and behavioral analysis to detect new threats and reduce false negatives.
4. AI-Based WAFs
Artificial Intelligence (AI) is the latest technology applied in threat detection for WAFs. AI can bring the benefits of automation, Machine Learning (ML), and decision-making into WAFs. An AI-based WAF’s core functionality is to perform in-depth data packet analysis to identify, learn, predict, and stop attacks logically. AI and ML routines can provide more accuracy to distinguish between legitimate and malicious traffic.Optimally, these types of WAFs can learn to establish whitelists and blacklists automatically, so there is no need to update signatures. Additionally, AI-based WAFs may adjust the baseline of standard behaviors to sharpen detection rules. Benefits?
- Reduce false positives and increase accuracy.
- Detect new attack variants.
- Higher performance. No need for signature updates.
- No need for human intervention (fewer errors).
5. Fully-Managed WAFs
Cloud-based WAFs are not a set-it-and-forget-it type of system that will give you the ultimate protection to your web app. A typical self-managed cloud-based WAF requires your involvement and full attention. You’ll have more control, but you also have more responsibility to:
- Update signature databases.
- Create security policies and rules.
- Set up behavioral baselines or application profiles.
- Create reports.
- Detect and identify,
- Alerting, and much more.
From a technical standpoint, a self-managed vs. fully-managed WAF is the same thing. What differs is the level of service. A fully-managed cloud-based WAF takes service to a whole new level. It will usually come attached with a response team and customer service that takes full responsibility for all (or most of) the control tasks described before.
The Fully-Managed Cloud-based WAF
An example of a cloud-based fully-managed WAF service is Cloudbric’s Smart Web Application Protection (Cloudbric WAF+).  Cloudbric’s SWAP is offered via a fully managed WAF service and can be installed in various server environments, including cloud, on-prem, or hybrid deployments.SWAP also comes with a robust logic-based detection engine, including built-in rules that supersede protection beyond the top ten OWASP threats. Want more website security?Check Cloudbric’s Cloud-Based Smart Web Application Protection.
Cloudbric’s SWAP is offered via a fully managed WAF service and can be installed in various server environments, including cloud, on-prem, or hybrid deployments.SWAP also comes with a robust logic-based detection engine, including built-in rules that supersede protection beyond the top ten OWASP threats. Want more website security?Check Cloudbric’s Cloud-Based Smart Web Application Protection.





