
Recently, a 2003 security report that was included in the National Institute of Standards and Technology (NIST) has resurfaced, bringing about an interesting discussion on strong passwords after one of the original writers, dubbed the “originator of [the] web’s password rules” by Slash Gear, has spoken on the matter.
The document highlighted the ways in which a secure and strong password should be chosen based on the following: a mix of capital letters, lowercase letters, special symbols, and numbers. The logic, back then, was that meeting these requirements would make it harder for hackers to crack passwords.
However, this writer has come forth and retracted his initial thinking, claiming that the advice he included in the report about creating a strong password in that particular way was largely based on a security white paper from the 1980s. This was long before online banking, social media, and smartphones became the norm, or before hackers developed creative ways to guess passwords with more ease.
With modern hacking tools and computing powers, hackers can simply use brute force attacks, for example, to guess passwords in a very short amount of time by systematically checking all possible combinations until they find a match. Because of this, the originator of password rules has offered alternative advice.
What makes a strong password?
Up until now we have been told to create strong passwords that are unfortunately hard for users to remember but easy for computers to guess. This concept is illustrated below by Randall Munroe, once part of NASA’s Langley Research Center.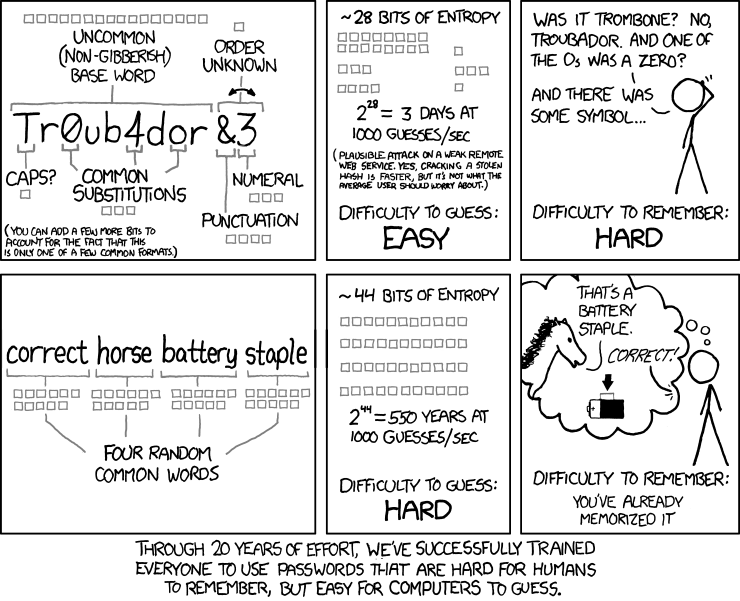 The writer of the document has recommended instead to make passwords long and easy to remember. This piece of advice only concerns online accounts that use one-factor authentication, but as a friendly reminder, the best online security practice these days is to rely on two-factor (2FA) or multi-factor authentication (MFA).Earlier last week, Dashlane published its Password Power Rankings survey, which revealed that 46% of the consumer sites they studied failed to implement the “most rudimentary password security policies.” In their evaluation of the sites, they looked at mechanisms for password strength assessment put in place by the sites. This included requirements for password length, password complexity and whether or not they were using 2FA and were capable of resisting brute force attempts. All of these are important security factors, but there is a major paradox that many aren’t discussing.
The writer of the document has recommended instead to make passwords long and easy to remember. This piece of advice only concerns online accounts that use one-factor authentication, but as a friendly reminder, the best online security practice these days is to rely on two-factor (2FA) or multi-factor authentication (MFA).Earlier last week, Dashlane published its Password Power Rankings survey, which revealed that 46% of the consumer sites they studied failed to implement the “most rudimentary password security policies.” In their evaluation of the sites, they looked at mechanisms for password strength assessment put in place by the sites. This included requirements for password length, password complexity and whether or not they were using 2FA and were capable of resisting brute force attempts. All of these are important security factors, but there is a major paradox that many aren’t discussing.
The Paradox
 While not all websites implement these so-called requirements upon account creation, sometimes users are prompted to create a “strong” password using a password strength assessment bar that helps test the strength of your password. Oftentimes users are required to create passwords with certain conditions that we saw earlier (special characters, mix of letters and numbers etc.), otherwise forbidding users to set up their accounts until these conditions have been met.Though as previously mentioned, creating a particularly complex password that satisfies these conditions poses a difficulty for the average user to remember. With the remaining 56% of sites enforcing all these password strength criteria, we’ve cultivated an online safety culture of emphasizing the complexity of passwords over lengthy passwords with the ease of recall.
While not all websites implement these so-called requirements upon account creation, sometimes users are prompted to create a “strong” password using a password strength assessment bar that helps test the strength of your password. Oftentimes users are required to create passwords with certain conditions that we saw earlier (special characters, mix of letters and numbers etc.), otherwise forbidding users to set up their accounts until these conditions have been met.Though as previously mentioned, creating a particularly complex password that satisfies these conditions poses a difficulty for the average user to remember. With the remaining 56% of sites enforcing all these password strength criteria, we’ve cultivated an online safety culture of emphasizing the complexity of passwords over lengthy passwords with the ease of recall.
Trying to shift everyone’s understanding of security now is going to be tedious change, but it’s an equally important step to take. We should be urging users to create lengthy and easy-to-remember passwords instead of misplacing their trust in complex but insufficiently long passwords that are actually nearly as susceptible to being cracked by hackers as a simple one of the same length.
Interested in reading more on the password topic? Head over to Slash Gear’s original article here. To take it up a notch in the realm of security, visit us to learn more about our web security services.





