
Nowadays the risk of web attacks is increasing, and cyberattacks, such as website forgery, tampering, and unauthorized access to personal information, can cause significant damage than what you expect.
Most would think of DDoS attacks or website forgery when they hear the word cyberattacks, but there are certainly more types of cyberattacks.
Here are some typical cyberattacks to watch out for in 2020:
- SQL injection attack
- Cross-site script (XSS) attack
- DoS/DDoS attack
- OS Command Injection attack
- LDAP Injection attack
- brute-force attack
- zero-day attack
1.SQL injection attack
SQL injection attack is an attack that sends out abnormal SQL scripts and manipulates the database via a web application. More specifically, hackers can gain access to your database by entering a SQL injection into the user ID/PW entry on the website. After accessing the database through a false command statement, hackers can create, delete, modify your data, and even shut down your entire system. In general, all websites that require membership or login should be careful because these sites are the main target of hackers as this can lead to massive personal information leaks.
2.Cross-site script (XSS) attack
This cyberattack exploits vulnerabilities in applications that are used by websites. Hackers would insert malicious code into the web page so when a user tries to access, an unauthorized page will appear. The main damage to a cross-site script (XSS) attack is that hackers can steal your cookies. A cookie is a text file that contains information about what the user has been doing on the internet. With the cookies, hackers can obtain user information, and not just that hackers can control the PC of a user by targeting browser vulnerabilities after executing successful malicious XSS attacks. So if your company’s PC has been attacked by an XSS attack, you need to be extra careful because hackers can steal information from your internal network as well.
3.DoS/DDoS attack
A DoS/DDoS attack is a type of attack where hackers send out lots of data at a specific server from multiple computers to paralyze it. A DoS attack occurs on a single computer, while a DDoS attack occurs on multiple computers. According to Cisco Systems’ Cisco’s Digital Network Shines in Rio 2016, 40 million security threats were observed, 23 million attacks were blocked during the Olympics, and 223 major DDoS attacks have been reported. When a website gets attacked by DDoS (indicated by abnormally large traffic), the service essentially gets paralyzed. And if you are a pay-as-you-go cloud user, you can be charged with a high cost. This method of cyberattacks has been going on for a long time, but it still remains as a major threat to businesses.
4.OS command injection
 An OS command injection attack allows the server to execute a malicious command. So, if a hacker executes a command to display the contents of a file, sensitive information can be stolen, and data forgery and SQL injection attack can occur. According to EQST 2020 Security Threat Forecast Report, there were 1.26 million OS command injection attacks in 2019.
An OS command injection attack allows the server to execute a malicious command. So, if a hacker executes a command to display the contents of a file, sensitive information can be stolen, and data forgery and SQL injection attack can occur. According to EQST 2020 Security Threat Forecast Report, there were 1.26 million OS command injection attacks in 2019.
5.LDAP injection attack
Lightweight Directory Access Protocol (LDAP) is a communication protocol used in accessing databases. This protocol helps businesses and individuals to find files on the private network. LDAP injection attacks maliciously manipulate LDAP queries to steal information such as usernames and passwords from the network.
6.Brute force attack
Brute force is a technique that attempts any combination of characters that can be used to identify a password. Even worse, hackers can automate this process of inputting thousands of passwords in seconds. There are several ways for hackers to break through your security, but brute force attacks can be fatal. For example, a four-digit number password can be found by entering 10,000 cases of numbers from 0000 to 9999. This can be done in a very simple way, so you should be careful. To prevent hackers from gaining information, you should find ways to detect abnormal growth in transmitted packets and monitor your application and network activity regularly.
7.Zero-day attack
It is called a zero-day attack because an attack occurs before the day of a security update of software vulnerabilities. In the absence of vulnerability protection, zero-day attacks can incur great damage to your business.In fact, it was reported that zero-day vulnerabilities were used for phishing, targeting crypto exchange in 2019.
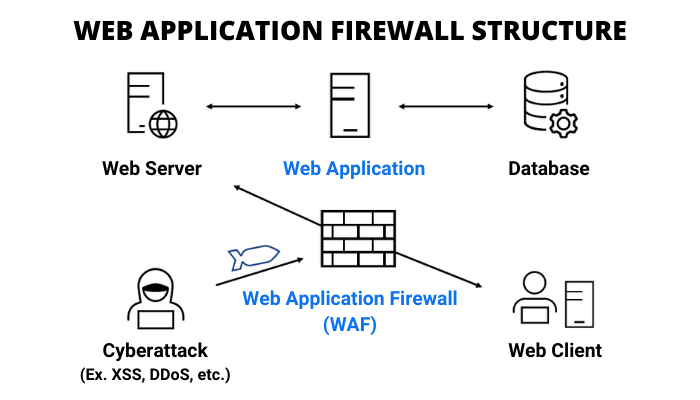 How to Respond to Web Attacks
How to Respond to Web Attacks
The types and methods of cyber attacks are evolving in many ways. For example, there are different types of attacks under the injection attack, such as SQL Injection, OS Command Injection, and so on. Oftentimes, identifying, and responding to these different types of cyberattacks is time-consuming and costly. That is why a solution to respond effectively to it is needed. Cloudbric is a company that offers affordable fully managed web security for users that are seeking solutions to protect their websites from these cyber attacks. Visit our site to learn more about our Cloud-Based Smart Web Application Protection (Cloudbric WAF+).





