
If you’ve been following us on Facebook, you know that we started a series called “Hacker Insight” where we explore topics and tech terms most frequently used in the hacker community. Along with a short description, we offer tips on how to stay protected from lesser known security threats. In this blog post, we will take a look at some of our most popular posts from the past year.
Hackers have a wide scope of methods and techniques to choose from when launching cyberattacks. Even unskilled hackers are able to cause significant damage by using plug and play computer scripts or codes developed by others to break into a system. The majority of hackers, however, are deliberate with their tactics, strategizing their delivery methods and who to target — most times with careful planning. For more on why hackers hack and the type of hackers you may come across online, make sure to check out our previous posts!
For now, let’s take a look at some of the attacks included in our “Hacker Insight” series. You might recognize attacks like ransomware and spear phishing, but have you heard of automated-input attacks or forced browsing attacks and what they can do to your website (or business)?

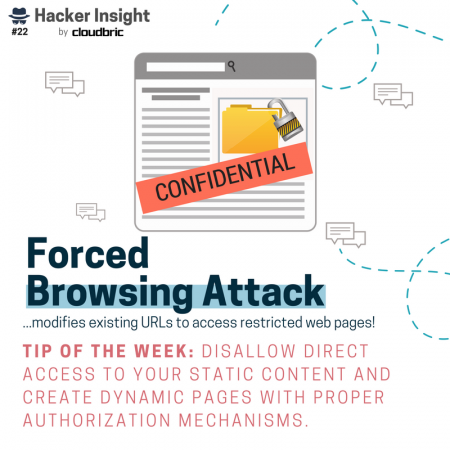
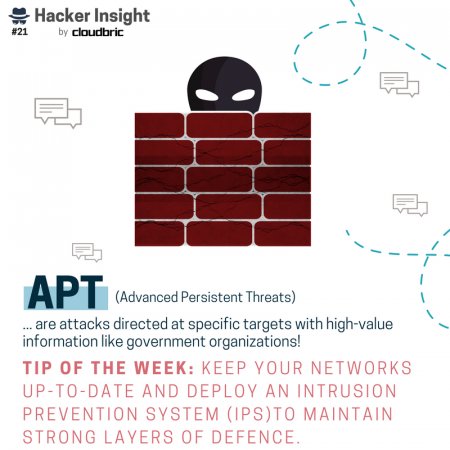
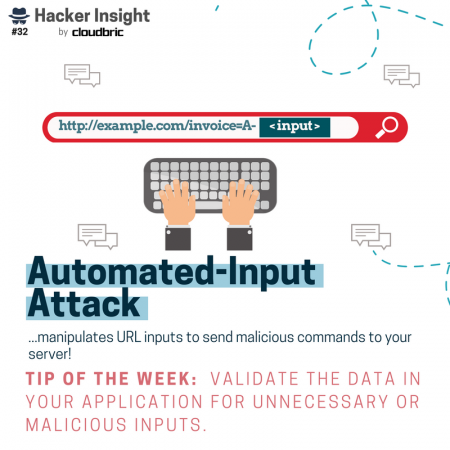
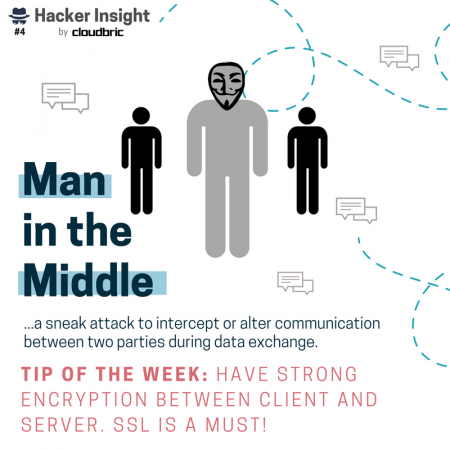

How do hackers launch these kind of stealthy attacks in the first place? We’ve got that covered too. Ways in which hackers gain access to vulnerable websites, networks, and devices include: web vulnerabilities like unsecure plugins, unsure Wi-Fi networks, vulnerabilities like zero-day, SQL injections, and so on!
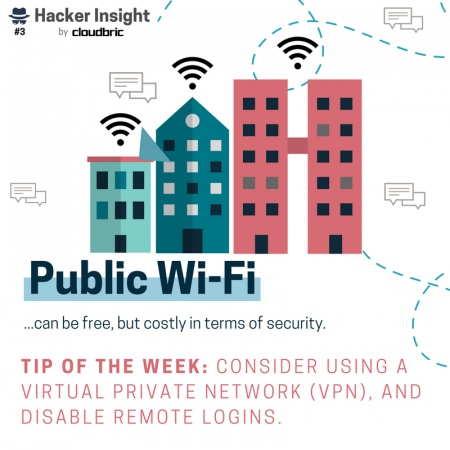
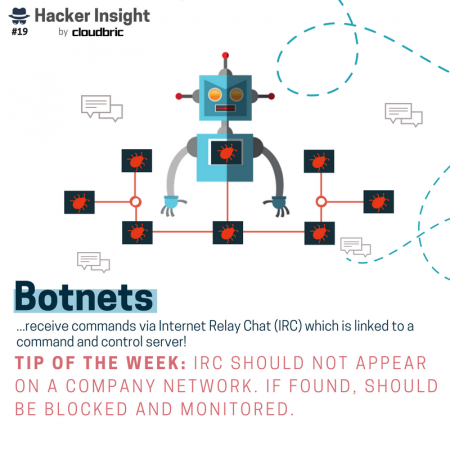
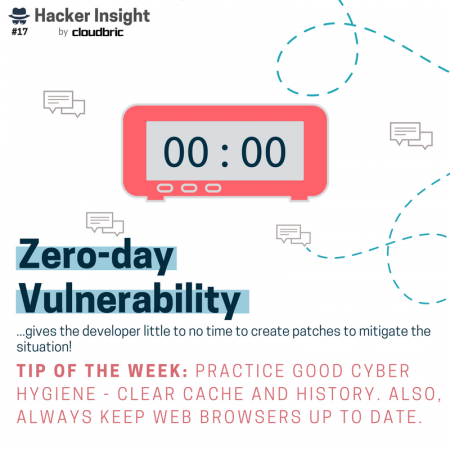
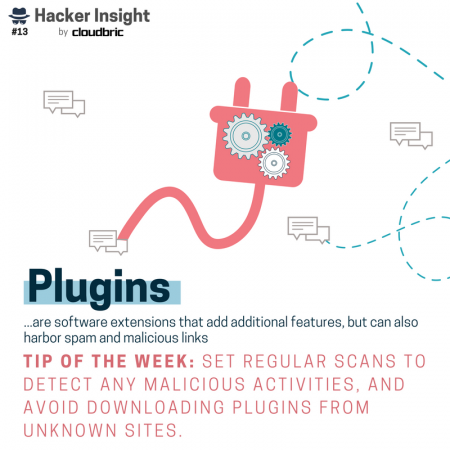
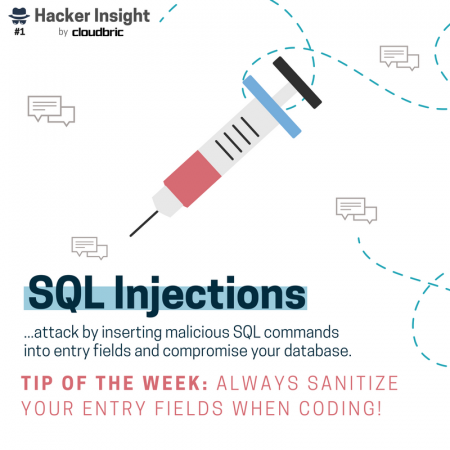
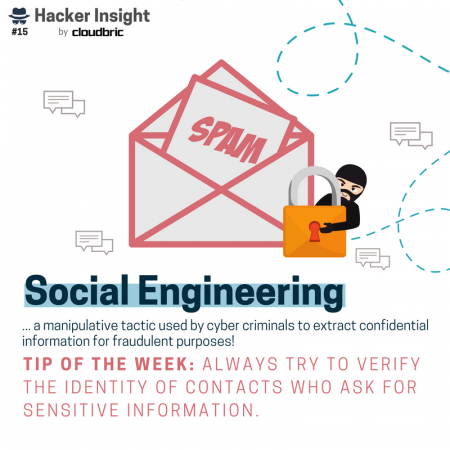
Of course the ways in which hackers can gain unauthorized access are many and not limited to the tactics above. Nonetheless, when it comes to cyber hygiene tips, it’s best to stay informed on the latest types of attacks.
We plan to cover wider range of hacker terms and provide more insights on how you can protect your privacy and websites. Check out our Facebook page for the full series and follow us now (if you aren’t already) to get weekly updates!





