In today’s fast-paced digital world, web security is no longer optional—it’s a critical component of online success. With data breaches and cyber threats on the rise, securing your website from malicious IP attacks is more important than ever. One of the most powerful tools at your disposal is AWS WAF (Web Application Firewall). By leveraging managed rules for AWS WAF, you can safeguard your site from suspicious traffic, block harmful requests, and maintain the trust of your visitors.
In this blog post, we’ll explore the ten biggest red flags that could indicate your website is vulnerable to malicious IP attacks. We’ll also delve into how managed rules for AWS WAF malicious IP protection can help you enhance your defenses. Let’s get started!
1. An Unusually High Volume of Failed Login Attempts
Why It’s a Red Flag:
An abnormal spike in failed login attempts could mean bots or hackers are systematically trying to guess credentials.
Actionable Steps:
-
-
- Implement Rate Limiting: Use AWS WAF rate-based rules to block repeated login attempts from the same IP address.
- Enable Multi-Factor Authentication (MFA): Add an extra layer of protection for all user accounts.
- Use Managed Rules for AWS WAF: Managed rules for AWS WAF malicious IP protection can automatically detect and block suspicious login requests.
-
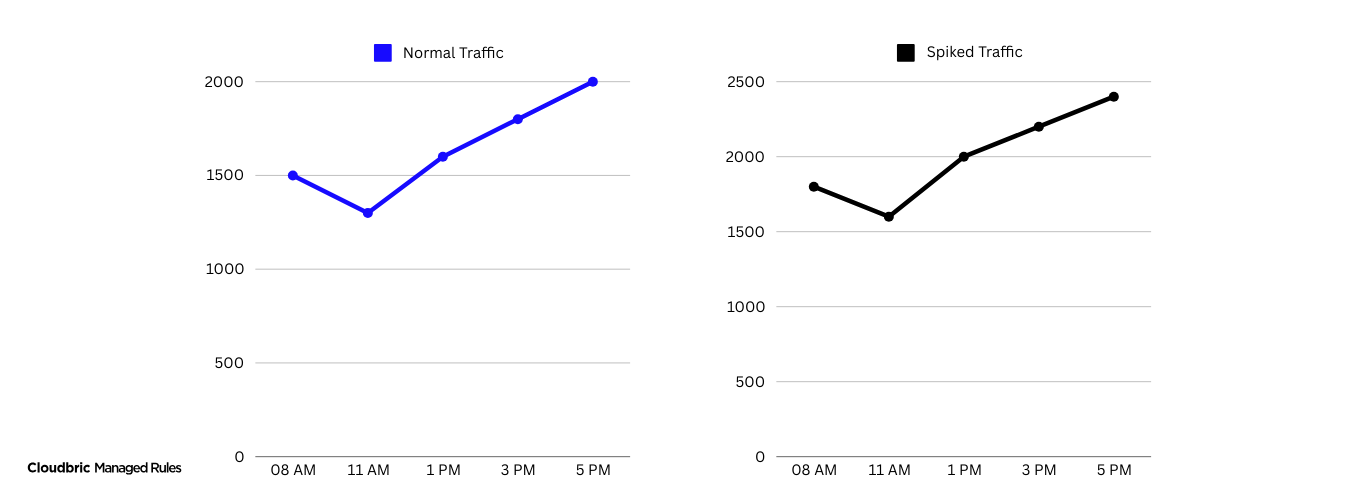
2. Frequent Traffic Spikes with No Clear Source
Why It’s a Red Flag:
Sudden surges in traffic without any marketing campaigns, social media mentions, or promotional activities often point to malicious IP attacks or DDoS (Distributed Denial of Service) attempts.
Actionable Steps:
-
-
- Set Threshold Alerts: Monitor real-time analytics and set alerts for unusual traffic patterns.
- Configure DDoS Protection: Consider AWS Shield Advanced alongside AWS WAF for comprehensive protection.
- Leverage Cloudbric Managed Rules: Utilize Cloudbric Managed Rules for AWS WAF Malicious IP Protection to help filter out harmful traffic surges automatically.
-
3. High Bounce Rate Despite Relevant Content
Why It’s a Red Flag:
If your analytics show a high bounce rate but your website content is well-targeted, bots might be crawling your site, or attackers could be testing vulnerabilities.
Actionable Steps:
-
-
- Review Analytics: Identify any sudden changes in bounce rate and correlate them with server logs.
- Block Known Malicious IPs: Employ AWS WAF IP match conditions to block repeated offenders.
- Tap into Managed Rules: Managed rules for AWS WAF ensure that known malicious IP addresses are automatically listed and blocked before they can wreak havoc.
-
4. Excessive 404 or 500 Errors
Why It’s a Red Flag:
A spike in 404 errors can indicate that bots are scanning for hidden admin pages or testing common vulnerabilities. Excessive 500 errors may signal your server is overloaded by malicious requests.
Actionable Steps:
-
-
- Audit Your Website Structure: Ensure your website’s structure and code are optimized and up to date.
- Limit Exposure of Admin Pages: Rename and secure admin directories to reduce the risk of brute force scans.
- Implement Managed Rules for AWS WAF Malicious IP Protection: Automated blocking of IPs that frequently trigger errors keeps your website’s performance stable.
-
5. Suspicious User Agent Strings
Why It’s a Red Flag:
Real users typically have standard user agent strings like “Mozilla/5.0” or “Safari/601.1.” Attackers often spoof or modify user agents to hide their tools.
Actionable Steps:
-
-
- Analyze Server Logs: Look for irregularities in user agent strings.
- Update WAF Rules: Configure custom AWS WAF rules to detect and block suspicious user agents.
- Adopt Cloudbric Managed Rules: With Cloudbric managed rules for AWS WAF, you’ll have up-to-date protection that recognizes new and emerging malicious patterns automatically.
-
6. Unprotected APIs and Endpoints
Why It’s a Red Flag:
APIs serve as gateways for data exchange. If they’re left unsecured, attackers can exploit them to gain unauthorized access or launch attacks.
Actionable Steps:
-
-
- Use Authentication and Tokens: Restrict access with API keys, OAuth tokens, or other authentication mechanisms.
- Monitor API Traffic: Track usage and set thresholds for anomalous requests.
- Use Cloudbric Managed Rules for AWS WAF – API Protection: Pre-built rule sets can help safeguard APIs against common exploits like SQL injection and cross-site scripting (XSS).
-
7. Slow Website Performance or Server Crashes
Why It’s a Red Flag:
Consistent slowdowns or crashes often point to malicious bots or IPs overloading your server with requests.
Actionable Steps:
-
-
- Optimize Server Resources: Check if your hosting environment is sufficient for your traffic levels.
- Deploy Caching Solutions: Use CDNs or caching to reduce server load.
- Enable Malicious IP Protection: Managed rules for AWS WAF malicious IP protection proactively blocks IPs generating excessive load.
-
8. Unusual Geographic Traffic Patterns
Why It’s a Red Flag:
If your customer base is primarily in one region but you suddenly see heavy traffic from unrelated locations, it could indicate a malicious IP attack.
Actionable Steps:
-
-
- Geo-Blocking or Geo-Filtering: Configure AWS WAF to block or challenge traffic from regions you don’t serve.
- Whitelist Legitimate Traffic: Maintain a whitelist of trusted IPs for approved partners or team members.
- Apply Cloudbric Managed Rules: Cloudbric managed rules for AWS WAF can help identify and block IP ranges known for cyberattacks.
-
9. Repetitive or Automated Requests to Sensitive URLs
Why It’s a Red Flag:
Attackers often test password reset forms, payment gateways, or admin panels by sending repeated requests.
Actionable Steps:
-
-
- Limit Request Rates: Employ rate-based rules to limit how often sensitive endpoints can be accessed.
- Enable CAPTCHA or Honeypots: Add an extra verification step to catch bots.
- Upgrade to Cloudbric Managed Rules: Cloudbric Managed rules for AWS WAF malicious IP protection can automatically detect abnormal patterns targeting your key assets.
-
10. Lack of Proper Security Updates or Patches
Why It’s a Red Flag:
Outdated plugins, CMS versions, or server software can contain known vulnerabilities, making your site an easy target for malicious IP attacks.
Actionable Steps:
-
-
- Regular Maintenance: Patch and update all software, including CMS, themes, and plugins.
- Use Vulnerability Scanners: Schedule routine scans for known vulnerabilities.
- Layer Security with Managed Rules: By combining regular updates with robust Cloudbric managed rules for AWS WAF, you’ll ensure ongoing protection against newly discovered threats.
-
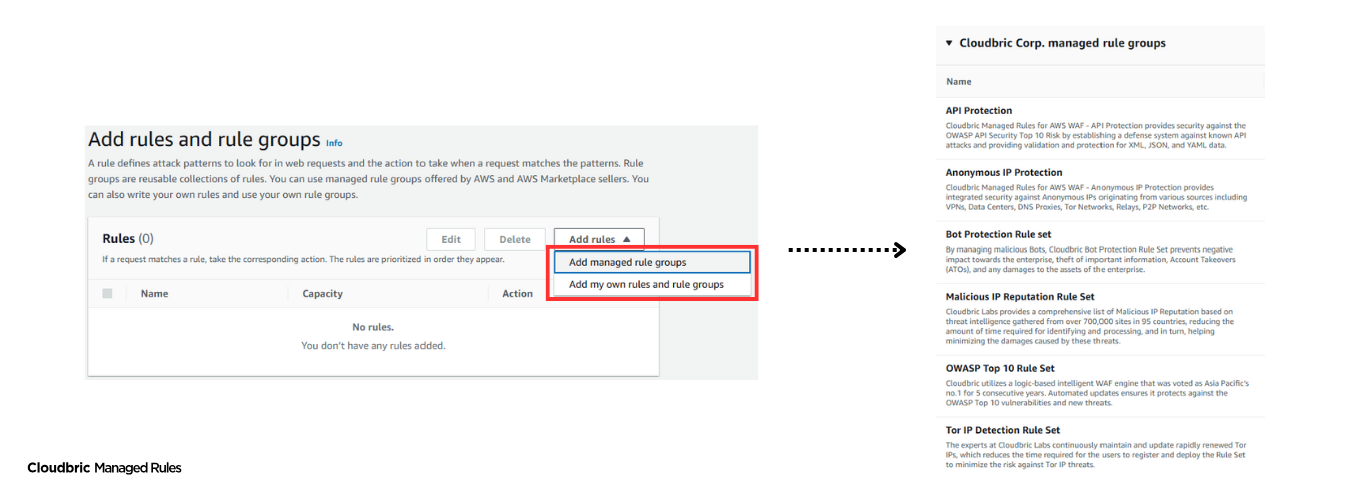
Introducing Cloudbric Managed Rules for AWS WAF Malicious IP Protection
When it comes to defending your website against evolving cyber threats, having the right security solution can make all the difference. Cloudbric Managed Rules for AWS WAF Malicious IP Protection offers a comprehensive, fully-managed rule set designed to protect you from the latest and most damaging IP-based attacks.
-
-
- Automated Detection & Mitigation: Real-time threat intelligence automatically updates your WAF rules.
- Easy Integration: Seamlessly integrate with AWS WAF without complex configurations.
- Advanced Analytics: Gain insights into blocked IPs, attack vectors, and overall threat profiles.
-
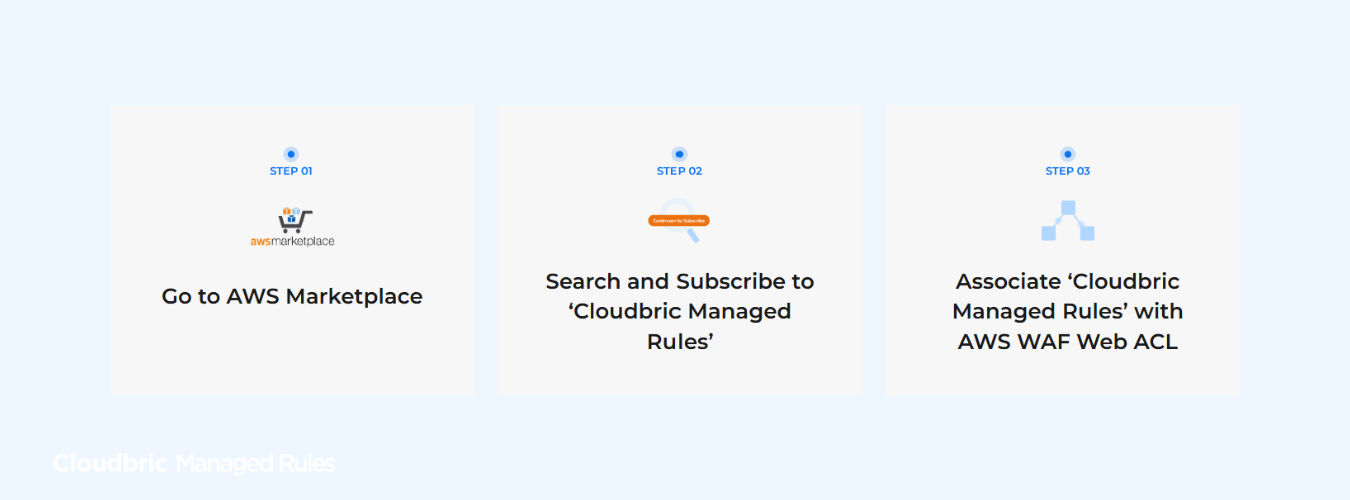
For more information on how to get started, visit our AWS Marketplace Product Link to explore how Cloudbric’s managed rules can work for you.
Conclusion
Staying ahead of malicious IP attacks requires vigilance, proactive monitoring, and the right security measures. By watching out for the ten red flags outlined above, you can identify weaknesses before cybercriminals exploit them. From AWS WAF configurations to managed rules for AWS WAF malicious IP protection, there’s a wealth of solutions available to bolster your web security.
Don’t wait for a cyberattack to highlight your vulnerabilities. Stay proactive—review your security strategy, update your defenses, and consider implementing Cloudbric Managed Rules for AWS WAF Malicious IP Protection for robust, real-time protection. After all, in today’s digital landscape, a secure website is the foundation of customer trust and business longevity.






